Top Five Methods of Yield Farming

TL;DR:
This blog post explores the five most common methods of yield farming in DeFi today: supporting network operations (staking), providing lending capital, providing liquidity to exchanges, delegating tokens to aggregators, and following protocol incentives. The benefits, risks, and considerations for each method are discussed, with emphasis on factors such as APY, counterparty slashing risk, token risks, economic rebasing risk, liquidity lockup period, and protocol incentives.
In the previous part of this guide, we looked at the meaning and purpose of yield farming. In this part, we look at the five most common methods of yield farming.
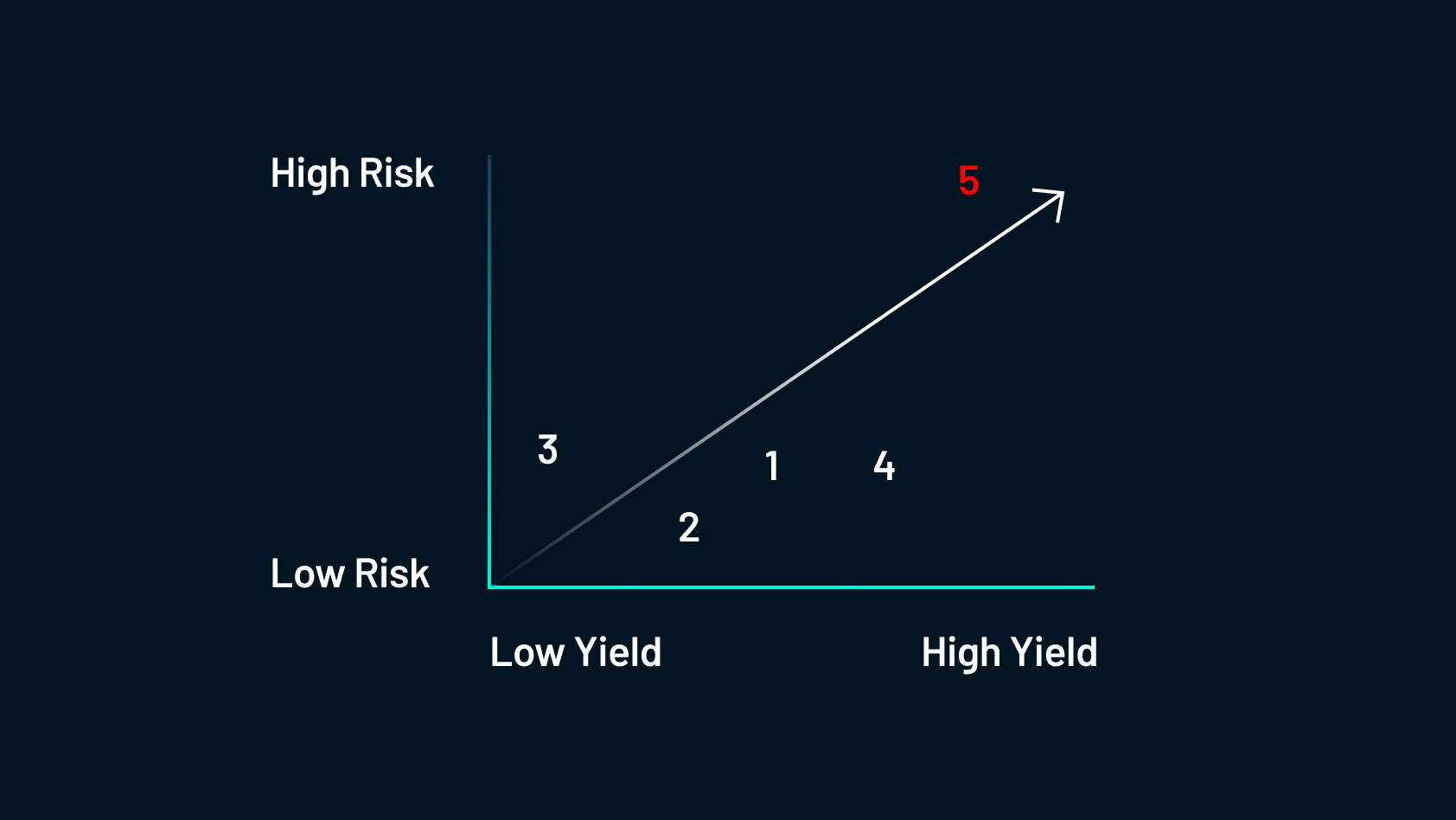
The five methods are: 1) Supporting network operations 2) Providing lending capital; 3) Providing liquidity to exchanges; 4) Delegating tokens to aggregators; and 5) Following protocol incentives. Let's look at each one and where they sit in terms of risk and reward.
1. Supporting Network Operations (Staking)
This is a fairly safe and predictable yield strategy. Here, farmers allocate their holdings to a network validator to allow the network to run more efficiently and securely. In return, they are paid by those who intend to use the network by staking.
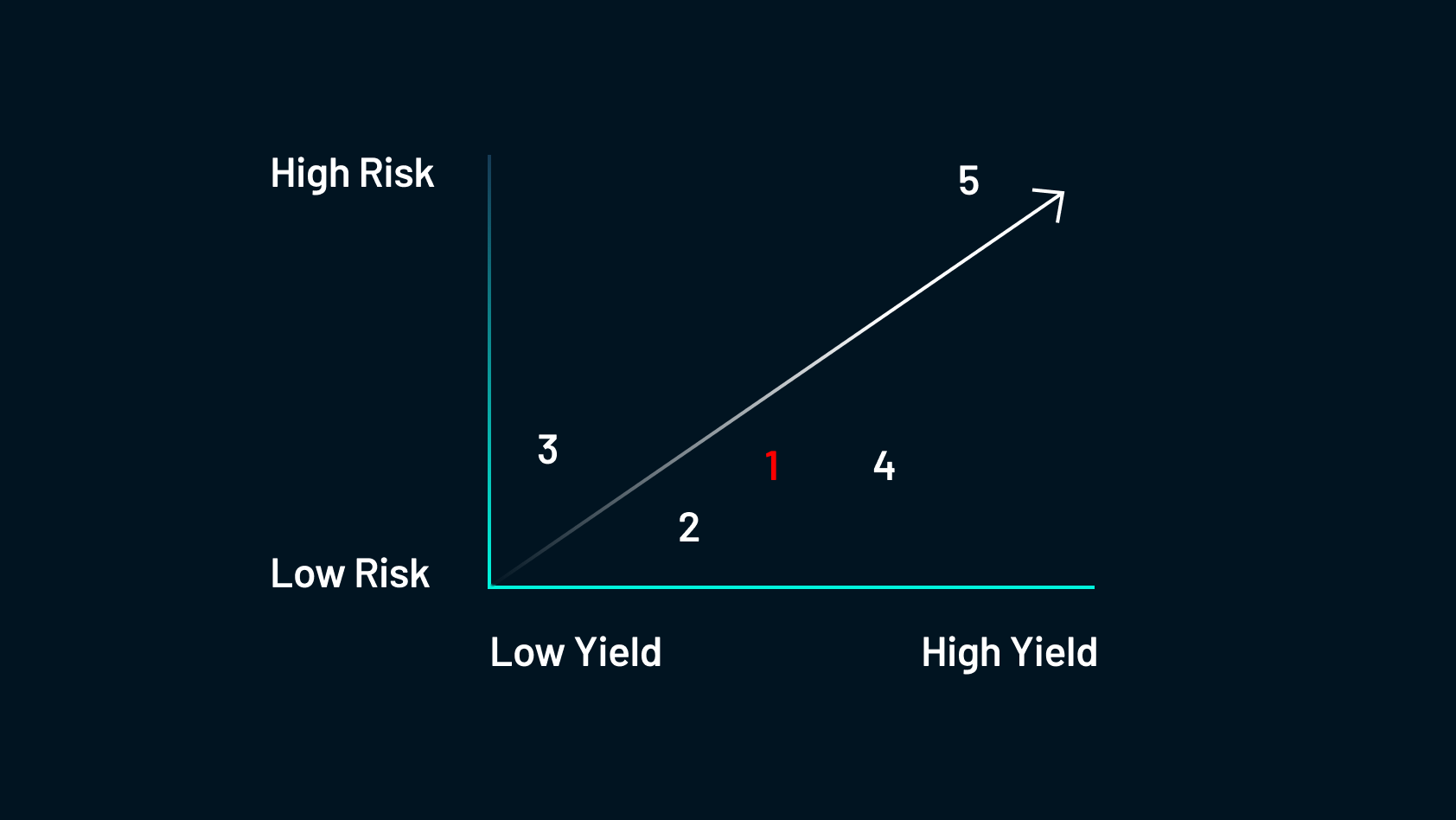
To illustrate this, imagine if Uber paid you to rent out your car for their drivers to use. In a way, you would be staking your car to the network to allow the network to run more efficiently and you would earn interest on your asset (your car) in return. When considering crypto staking, there are several different options: custodial, decentralized, and liquid staking.
- In custodial staking, you offer your tokens to a third party and they perform actions on your behalf. Crypto exchanges like Coinbase or Binance are custodial.
- The benefits of custodial staking are that it’s great for beginners, with relatively easy onboarding and (usually) decent liquidity.
- The risks of custodial staking include comparatively less transparency and reduced APY.
2. As the name suggests, if you choose decentralized staking, the activities are carried out in a decentralized manner. In this case, you would most likely run your own node on the network and act as a validator yourself.
- The benefits of decentralized staking include full control of assets, higher APY, and the fact that it promotes network decentralization.
- The risks of decentralized staking include the facts that you must maintain your infrastructure, your assets are illiquid, and you can be exposed to counterparty slashing (more on this later). Also, there is little to no regulatory oversight, customer protection or customer support in the traditional sense, and often no customer support – no one is responsible but yourself.
3. Building on decentralized staking is another concept called liquid staking. Since the minimum amount of cryptocurrency required to engage in staking can be high for some protocols, several users may pool their funds together and delegate them to a trusted actor. When engaging in liquid staking, the protocol gives you a derivative asset in exchange for staking your real assets. This derivative asset is like an IOU that can be exchanged for the original asset when you unstake. In this way, although your primary asset is locked, you retain your liquidity through the derivative asset. This derivative asset is a liquid token that you can use for other yield farming strategies. When you unstake your tokens you exchange the derivative asset for your initial asset.
- The benefits of liquid staking include ease of participation, it doesn’t require infrastructure, assets are liquid, and it can promote decentralization.
- The risks of liquid staking involve a lower APY, reduced decentralization, and that it exposes to counterparty slashing.
Staking generally requires a minimum amount of staked tokens that must be locked up for a period. Liquid staking can be good for decentralization because a user without the minimum number of tokens for fully decentralized staking can still participate without utilizing a centralized, custodian account. However, if many users elect to delegate their tokens to the same validator, those tokens become more centralized.
Considerations before staking
While staking is generally a low-risk, mid-yield activity, there are several considerations that prospective stakers should keep in mind before deploying their assets. Please note that some of these considerations will also apply to some of the other methods of yield farming.
APY: This is fairly self-explanatory, but if you are considering staking your tokens it’s important to know the APY even if it will change over time. Consider the amount of rewards you expect to receive through staking, and weigh these rewards against the other considerations to ensure that the reward is worth the risk.
Counterparty Slashing Risk: This risk is specific to staking. Participants in Proof of Stake (PoS) cryptocurrency networks (validators, block producers, delegates) are trusted to maintain the integrity and security of the network. They are required to stake a minimum amount of cryptocurrency as collateral to be able to contribute to network operations. In return for performing properly, they receive staking rewards. However, if they behave maliciously or otherwise violate the rules of the network, penalties will be levied in the form of slashing. Slashing typically involves punishing the participant by permanently destroying or confiscating a portion of their staked funds. The degree of slashing depends on the severity and nature of the offense and varies by protocol. Slashing commonly occurs due to double-signing (signing conflicting blocks), censorship, or other types of malicious behavior that undermine the network’s consensus. So, although staking may seem like a safe method of earning yield, users should be mindful of those to whom they delegate their funds. If you have delegated your assets to a validator who is slashed, you will lose your funds as well! Be sure to do your research when choosing a specific validator to support.
Inherent Token Risk: These risks are typically associated with the characteristics, design, and underlying technology of the token itself. These risks will apply to all cryptocurrencies. Here are some examples of inherent token risks and their relation to staking:
- Market volatility: The value of many cryptocurrencies can experience rapid and significant fluctuations due to factors such as market demand, speculation, regulatory developments, or macroeconomic conditions. This volatility can easily counteract the rewards gained from staking if one is not careful.
- Regulatory risks: Regulatory uncertainty and changes pose risks to cryptocurrencies as well as staking. Different jurisdictions have varying approaches and regulations regarding cryptocurrencies and staking, which can impact acceptance, usage, and trading. Regulatory actions, such as bans, restrictions, or unfavorable regulations, could pose risks to specific tokens as well as their ability to be staked.
- Technological risks: Tokens rely on blockchain technology, which is still evolving. Vulnerabilities or flaws in the underlying protocols or smart contracts used for staking can lead to security breaches, hacks, or exploits. These risks can result in the loss of funds, manipulation of token supply, or other adverse consequences for token holders and stakers.
- Governance and consensus risks: Tokens that are part of decentralized networks often involve community governance, consensus mechanisms, and even staking. The decision-making processes, such as voting or consensus algorithms, can be subject to manipulation, centralization, or conflicts of interest. Disagreements among token holders or community members may result in contentious hard forks, contentious governance decisions, or network splits, which can affect the value and viability of the token and its ability to be staked.
- Adoption and utility risks: The adoption and utility of a token can impact its value and success. Factors such as network usage, real-world applications, partnerships, developer activity, and user demand play a significant role. Tokens that fail to gain adoption or offer meaningful utility may struggle to maintain value or achieve their intended purpose.
- Liquidity risks: Tokens with low trading volumes or limited availability on exchanges may experience liquidity risks, making it challenging to buy or sell your token and token staking rewards at desired prices if at all.
Economic Rebasing Risk: Some cryptocurrency protocols will periodically adjust the supply of tokens in the network based on preset formulas or rules, a practice known as economic rebasing. The purpose is to maintain price stability and reduce volatility. To accomplish this, the token supply of each holder is increased or decreased proportionally. If the price of the token is consistently higher than the target value, the mechanism may decrease the total number of tokens available by removing a proportional amount from everyone. Conversely, suppose the price of the token is consistently lower than the target value. In that case, the mechanism might increase the total number of tokens available by adding a proportional amount to everyone.
You may encounter a protocol offering a very high APY for their yield farm. While participating in this farm, you might receive a large number of tokens. However, if economic rebasing is employed, the total value of your holdings might not increase even though you hold more tokens. Instead, only the number of tokens you hold increases, resulting in an increased ownership percentage of the total number of tokens. This means that you effectively own more of the network itself even though the value of your holdings remains constant.
Liquidity Lockup Period: Some protocols employ a lockup period — a predetermined timeframe in which a liquidity provider cannot withdraw or transfer their liquidity. This is used to ensure stability and constant liquidity by incentivizing liquidity providers to commit their assets to the platform for a specific duration. It is important to know how long this period is before deploying capital to a protocol.
2. Providing Lending Capital
This describes the process of farmers allocating their holdings to capital-constrained borrowers in return for fees that can be subsidized by the network. This is likely the safest form of yield farming and the process is similar to a bank offering a loan.
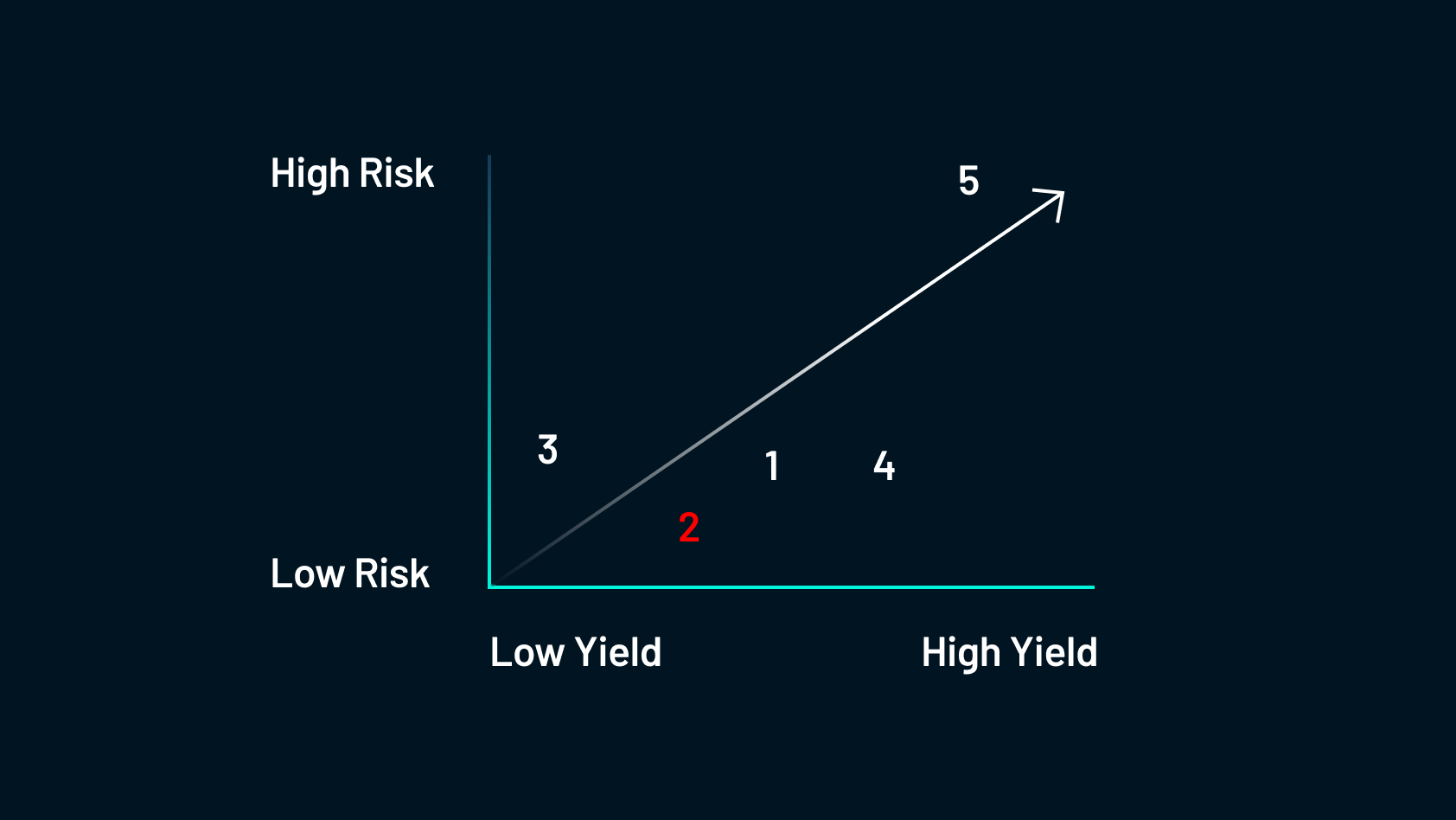
The safest opportunity would be over-collateralized lending, and a few examples of such protocols are $AAVE, Compound and Maker DAO. More information on this topic can be found in a previous Shimmer DeFi Education Series post Session #3 (Part 1): DeFi Lending & Borrowing.
The benefits of providing lending capital include speed, liquidity, permissionless, and relative safety. Questions to ask before lending capital include:
- Is there a lock-up period for your deposited funds?
- Is there protection against insolvency?
- Is over-collateralization (if applicable) appropriate for you?
- Have the smart contracts been audited, and by whom?
- How stable are the fees?
3. Providing Liquidity to Exchanges
To recap, farmers provide liquidity to centralized exchanges in return for trading fees or native tokens.
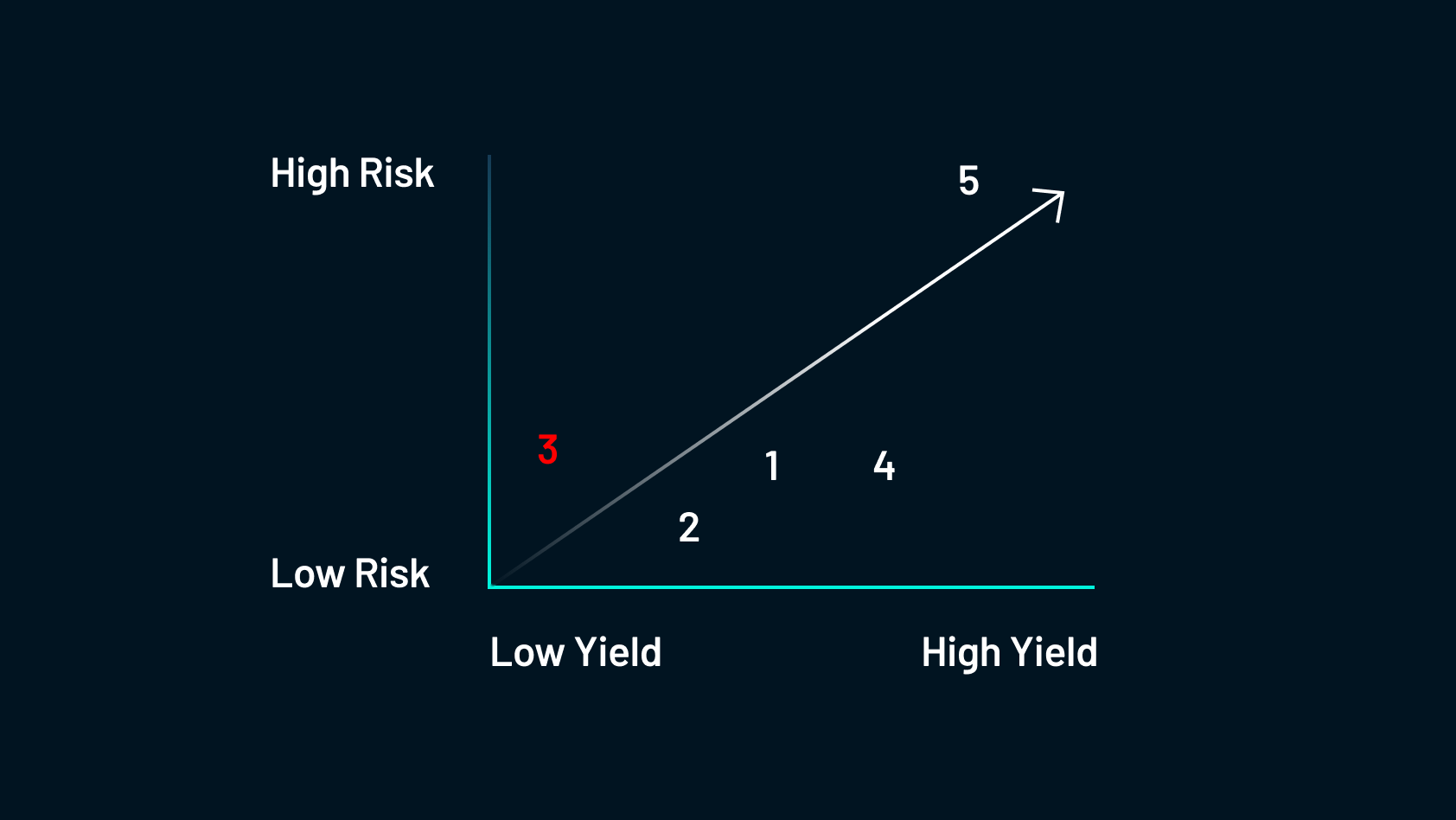
The biggest risk that you’re going to encounter is impermanent loss. This describes the opportunity cost of being a liquidity provider compared to simply holding the initial assets instead and was explored in detail in the Shimmer DeFi Education Series Session #2 (Part 3): Token Swaps — DEX vs. CEX.
The benefits of providing liquidity to exchanges are that anyone can participate (it is permissionless) and there is a high potential for yield. Questions to ask before providing liquidity to exchangesinclude:
- What is the split fee on the pool?
- In what currency are the fees paid? Are you being paid in a native currency or a different token? What is the risk for impermanent loss?
- What is the actual trading volume of the pool? Are people using the pool?
- What are the underlying token risks? (see the relevant portion of Staking considerations)
4. Delegating Tokens to Aggregators
The risk here is fair for a decent yield. If there is a yield farming strategy that anyone could do confidently, it would likely be delegating tokens to aggregators.
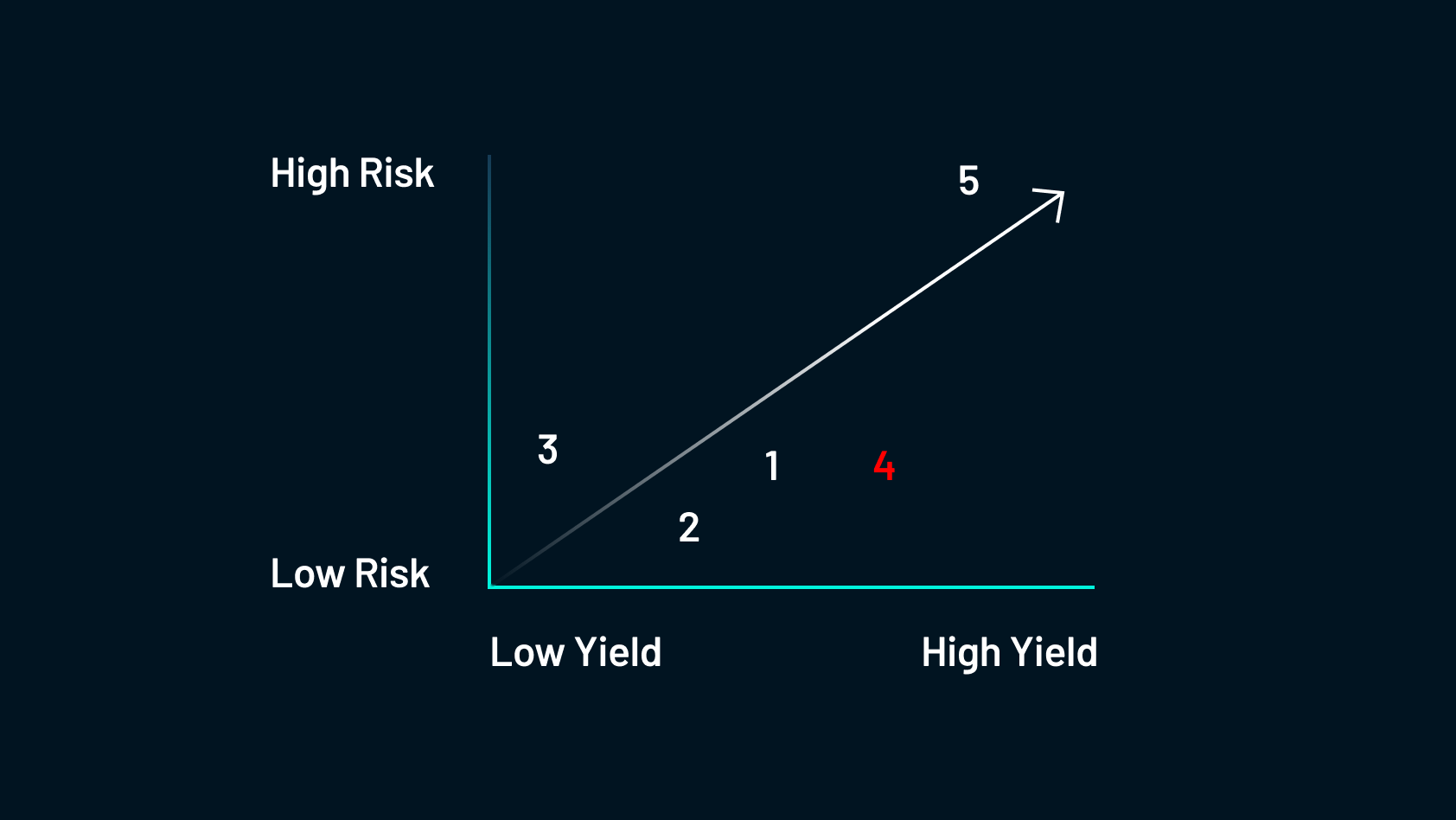
This process involves farmers providing their tokens to aggregators to take advantage of economies of scale for lower transaction costs and higher returns. To do this, a user would deposit their tokens into a single smart contract for yield farming or other DeFi transactions. Doing this collectively results in lower costs and higher returns. It’s fairly safe but there is a distinction to be made between a true aggregator and an auto-compounder.
A true aggregator combines and consolidates various DeFi protocols and services into a single interface. It allows users to access and interact with multiple protocols, trade assets, provide liquidity, and access various DeFi services within a unified platform. A true aggregator offers benefits for passive yields, passive benefits, variety in strategies, socialized gas costs, etc. Yearn is a good example here. They have vaults where you can deposit your DAI, USDC, ETH, etc. and they give you a fixed APY in return. One downside here is that they take a small fee off the top. Also, there’s composability risk: you don’t necessarily know the strategy that they’re utilizing. While you can dig into their documentation and attempt to figure it out, they’re still using multiple smart contracts that could have inherent risk.
An auto-compounder optimizes yield farming strategies by automatically compounding users’ funds. It identifies the best opportunities for yield generation across different protocols and performs automated compound actions to maximize returns. The primary function of an auto-compounder is to automate the process of reinvesting and compounding rewards earned from yield farming. An example of such a protocol is Convex. By allowing an auto-compounder to manage your funds, it collects the rewards automatically regularly and reinvests them for you. This aggregates your rewards and allows you to earn rewards on your rewards. There’s still the underlying token risk but it’s a little larger here because you’re only generating yield from one specific source. An auto-compounder like this will typically have governance or other incentives in mind. They’ll focus on a single token to try to obtain enough to influence governance decisions.
Questions to ask before delegating tokens to aggregators include:
- Is the protocol you are considering a true aggregator or is it an auto-compounder? Which is more appropriate for you?
- Where are the sources of yield?
- What are the strategies being taken? It’s always good to understand the token flow and there should be a diagram that illustrates this.
- How risky is the strategy of the protocol?
- Is there any issue with composability?
- Have the smart contracts been audited, and by whom?
5. Following Protocol Incentives
This structure is a high-risk, high-reward approach in DeFi. Farmers increase awareness and usage of a protocol and receive rewards in exchange. These rewards are offered as a way to seed new networks.
For instance, the Arbitrum Odyssey protocol guides users through its ecosystem, providing various incentives and rewards like NFTs and airdropped tokens. The goal is to familiarize users with different products and encourage their adoption within the network.
On the other hand, $AAVE on Avalanche demonstrates a different approach. By subsidizing extra APY with Avalanche tokens, $AAVE incentivizes users to bring liquidity to the Avalanche network. This strategy aims to attract users to a new ecosystem and offers benefits like free tokens and the highest yield opportunities.
However, it’s important to consider the risks associated with these incentives. Firstly, the tokens received as incentives may not be known in advance. Secondly, the long-term value of the protocol and its associated network is uncertain. Protocols offer these incentives to attract capital and bootstrap their networks. In the end, it’s crucial to conduct thorough research and due diligence to ensure you’re not investing in a Ponzi scheme or falling for deceptive practices. Understanding the goals and risks of protocol incentives is essential for making informed investment decisions in the DeFi space.
Questions to ask before following protocol incentives include:
- Where does the yield come from, and is it sustainable? Be careful of extremely high yields, because it could be due to rebasing. At the same time, it could be a token that has no value. Don’t get enticed by promises of large amounts of tokens, because a large number times 0 is still 0.
- Is there any specific platform risk? For example, if we are considering Solana and the network experiences one of its outages, would you be okay with potentially losing the ability to remove your capital for some time?
- If you’re moving your capital from one network to another, how strong is the bridging risk? Have the bridges been in use for long enough without a hack that you have faith in using them? (See the Lindy Effect discussion in the next section.)
Now that we’ve fully explored the five common methods of yield farming in DeFi, it should be clear that there is likely an opportunity for farmers of any risk profile and target yield. However, with all the protocols that are currently offering yield farming and the many more entering the market every day, savvy farmers will need to utilize effective tools to identify the best protocols for them. In the next section, we discuss a couple of ways that you can assess a protocol on your own before exploring three different popular tools that can assist you.
Beginner’s Guide to Yield Farming
Part 1: Seeding Success: The Power of Yield Farming in Crypto Networks
Part 2: Top Five Methods of Yield Farming
Part 3: Research and Analysis Tools
Also in this series
Crypto Wallets
DEX vs. CEX
 iota-news.com
iota-news.com
