Another day, another rug pull: decentralized finance protocol that offered 103,000% APY allegedly falls victim of rug pull; team keeps silence.
Titano Finance liquidity pool drained for $1.9 million
According to the statement shared in the official Twitter account of Peckshield blockchain security provider, Titano Finance DeFi protocol has seen one of its elements exploited.
#rugpulls PeckShield has detected @TitanoFinance is rugged: the owner sets the PrizeStrategy contract, which then drains about 4,828 BNB (~$1.9m)! The rugged funds were initially held in this wallet 0xad9217e427ed9df8a89e582601a8614fd4f74563 and then split into 24 addresses. pic.twitter.com/vrGbLLspGo
— PeckShieldAlert (@PeckShieldAlert) February 14, 2022
A total of 4,828 Binance Coins (BNB), or $1.9 million, were transferred from The PrizeStrategy contract, i.e., the key instrument of its liquidity ecosystem.
In almost no time, the price of TITANO lost 80%: in less than 20 minutes, TITANO/USDT rates plummeted from $0.16 to $0,03. By press time, TITANO managed to surge to $0.12.
Titano Finance (TITANO) aggressively promoted itself as "The Best Auto-Staking & Auto-Compounding Protocol in Crypto." It offered eye-watering APY of 103,000% to its clients.
Hack instead of rug pull?
Surprisingly, some Twitter users are denying the fact that the team of Titano Finance (TITANO) rugpulled their customers. Numerous accounts are tweeting that the protocol fell victim to a third-party attack.
As per their statements, the account behind the exploit was involved in attacks on Arbix DeFi and Bunny Finance protocol, and even on centralized services BitMart and AscenDEX.
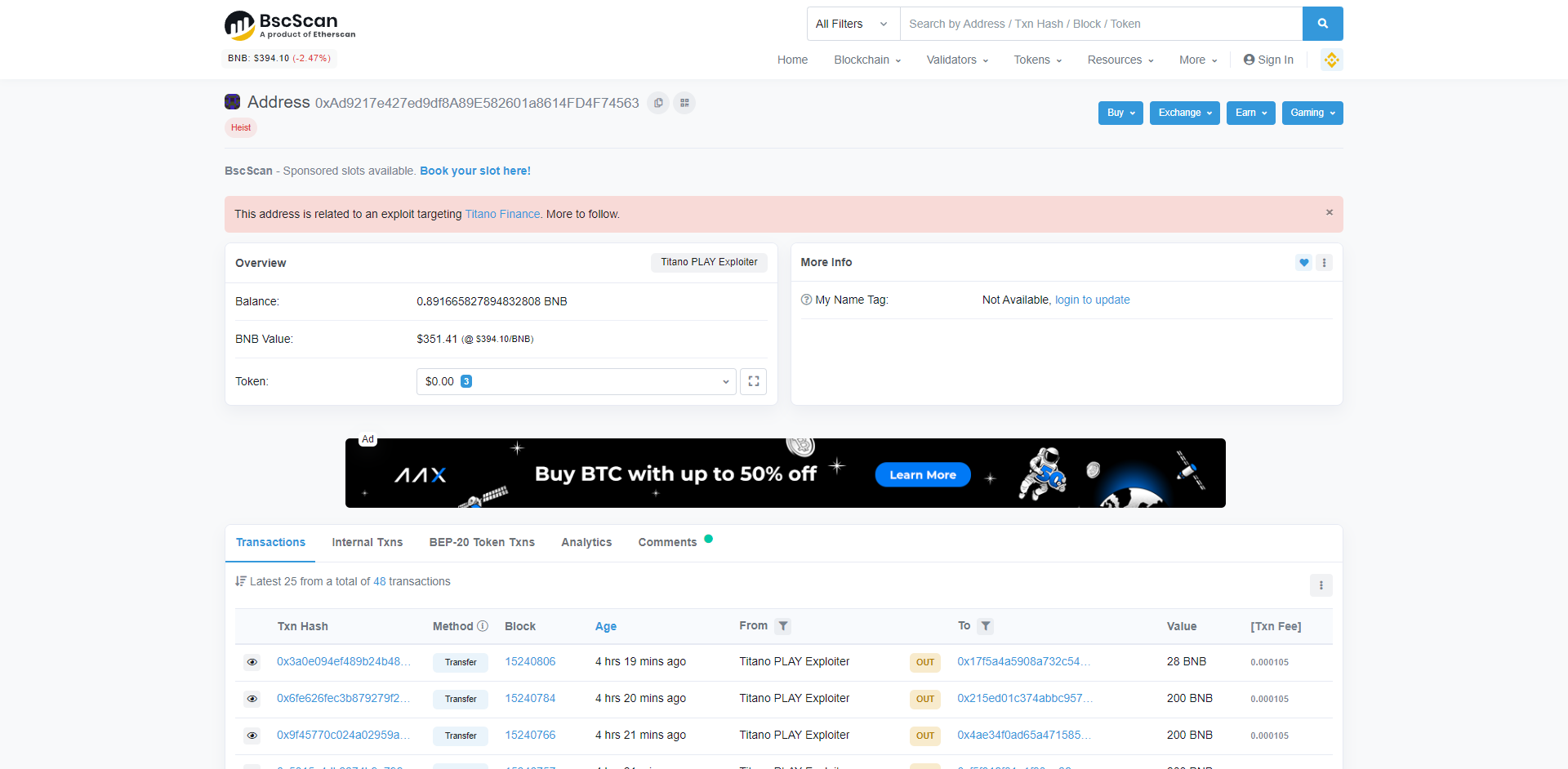
They assure users that the address role in previous attacks was confirmed by flags on BSCScan, but it is not. Leading Binance Smart Chain Explorer only sees the infamous 0xAd9217e427ed9df8A89E582601a8614FD4F74563 address as a "Titano PLAY Exploiter."
 u.today
u.today