Authentication: The Door To The Digital World
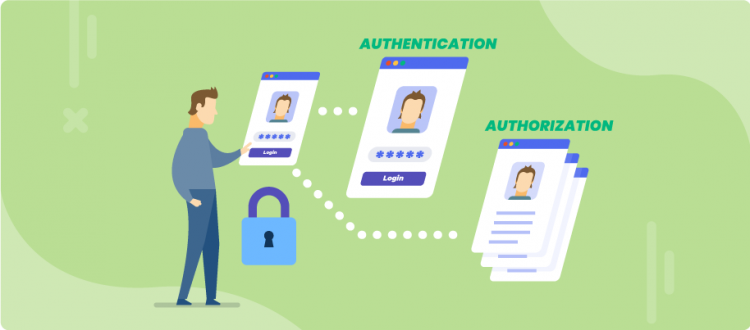
Identification, authentication, authorization, verification — all these terms are associated with one process: connecting person to digital services. Where did they come from and what do they mean? Let’s find out about the difference between them and learn why understanding of their essence is so important for any person.
Discover
Identification means "recognition" of a particular person, or rather, his or her identification number and related records in the database. In general, this concept has a broader meaning. In philosophical discourse, for example, it describes how a person relates to himself and how he defines himself in this world.
Introduce Self
Authentication is a better concept. It describes how a person “appears” to a system which recognizes him or her by analyzing the received data. The word "authentication" comes from the Greek αὐθεντικός — "authoritative", "genuine", which in turn came from the word αὐτός - "self." Thus, authentication is a process that a person initiates when deciding to participate in a digital service and connect to it.
There is a personal account “John Smith” in the database service, associated with “qwerty” entry. If a person entered a password during the authentication process, then it can be confirmed using the “qwerty” symbols by the computer for its authenticity. This will be followed by providing the user with access to the service resources and rights to perform any actions. The exact process is called authorization.
Access
A certain set of rules and restrictions which corresponds to a specific user is formed in the computer system: he or she is given permission to view certain information and to make changes to any data within authority — which is authorization.
The practice of using authorization in financial services (for example, when using bank cards) introduces a little confusion into this rather simple and understandable definition.
When making contactless payments, the cardholder applies it to the terminal and doesn’t enter any passwords. For a payment system, the person who holds the card in his hands is an authenticated user only due to the very fact of owning a piece of plastic with a chip inside. However, when paying for a purchase in excess of a certain limit (usually $25), the system will require a password: it will not authorize the user due to the increase of authority level to spend funds on the account.
It is clear that in each particular case of using the identification-authentication-authorization connection, the boundaries between these processes are blurred and it is very difficult to keep track of exactly where one goes to the other. Engineers, security specialists, marketers and sellers create and configure their user interaction systems, focusing not on strict definitions, but in such a way as to get the maximum benefit and provide their customers with a pretty simple and comfortable service.
At this point, there is a conflict and contradictions: for example, the easiest way to authenticate is to get rid of the password at all. Why to remember or write down these characters? Entering your name into the form is much easier. However, it is obvious that a password is a necessary security measure that must be taken, complicating the life of the user and the technical part of the services.
Although this is an indisputable statement: as described in the example with contactless payments, it is possible to free the consumer from the need to remember and enter codes.
Problems
A user who enters name and password into the form, in addition to access to the opportunities provided by the service, gives the computer system the opportunity to manage the profile — a digital representation of personality. Any actions in this system and data sets are now associated with this particular person. For example:
- social network — personal data, photos, messages, friends list;
- bank account — data on the amount in the account, transaction history, official information about the place of residence, insurance numbers, phone numbers, documents;
- insurance or medical service — in addition to everything, a medical history, information about the current state of health.
To sum up, we can say that services are attacked, user passwords are in the hands of craftsmen who have knowledge and experience of penetrating computer systems. The more systems, the more potential data leaks.
One for all
The loudest facts of hacking and user data leakage are well known, and their number is not getting less. Special cases and less massive leaks, as a rule, are not advertised, but for each affected person they do not become less painful.
One way to deal with a variety of companies that store user passwords is to create unified authentication systems. An example of this approach is the method of connecting to services using a social network account or information system.
I manage it on my own
A relatively new approach that solves the problem of centralization — a system of distributed storage and cryptographic protection of user data. In such services blockchain technologies are often used. A person uploads personal data and documents, which are encrypted using reliable cryptographic algorithms and are recorded in a storage system based on a distributed ledger.
This way of using sensitive information is one of the most promising and reliable, but it also has drawbacks. For example, a small prevalence. Another bad side which incidentally is also characteristic of other methods is the very procedure of authentication, proof of a person’s authenticity, determination and confirmation of a fact.
The next article will be devoted to the f problems and solutions of the verification procedure (another complex concept from the slang of programmers).
Image courtesy of Swoop