A total of 149 million login credentials were exposed. The data leaked access to 420,000 Binance accounts, Instagram, Facebook, Roblox, dating sites, and other platforms.
The database exposed to the public lacked encryption and password protection, according to Jeremiah Fowler from ExpressVPN. It included 149,404,754 distinct login credentials and reached 96 GB in size of raw data.
The leaked data was open to the public
The database was open to the public. Anyone who found it could access millions of people’s credentials. The exposed documents contained emails, usernames, passwords, and account login URLs.
The leaked records included data from social media websites like Facebook, Instagram, TikTok, and X (formerly Twitter). Dating apps and OnlyFans accounts data revealed login methods for creators and users.
Fowler found leaked logins from many streaming accounts as well, such as Netflix, HBO Max, Disney+, and Roblox.
In the small sample of records the cybersecurity researcher examined, he found financial service accounts, crypto wallets, Binance trading accounts, as well as banking and credit card logins.
Government accounts were not spared either. Logins linked to [dot]gov domains from various nations were found. Such sensitive data may enable targeted phishing or impersonation attacks. This could threaten national security and public safety.
The database was hosted online but lacked ownership details. Fowler reported it to the hosting provider, and after almost a month, the hosting was suspended. The hosting provider refused to reveal who managed the database.
It remains unclear whether the database was used for criminal activity, legitimate research, or why it was publicly exposed. The database exposure duration is unknown. Other people might have accessed it.
A troubling detail is that the records kept growing until they became restricted and inaccessible, the cybersecurity researcher added.
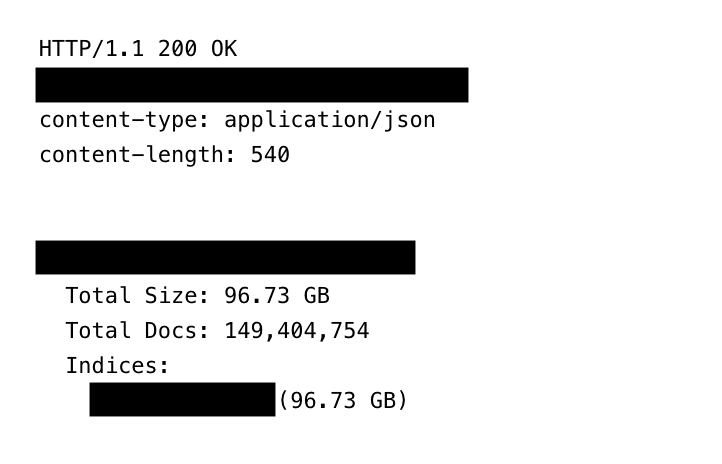
Infostealer malware collected logins and extra information
The database contained keylogging and infostealer malware, which secretly collect credentials from infected devices.
Unlike old infostealer malware datasets, these files recorded extra information. The records contained the “host_reversed path.” This structure organizes stolen data by victim and source for easy indexing. Reversing the hostname can prevent directory conflicts and evade simple detection rules targeting common domain formats.
The system assigned each unique log line a document ID based on a line hash to guarantee one distinct record. A brief check showed these hash and document IDs were unique with no duplicates found.
The release of many unique usernames and passwords creates a major security threat for many people who are unaware that their data was compromised. Criminals may use this information to automate attacks on accounts like email, crypto wallets, social media, and business systems. This greatly raises the risk of fraud, identity theft, financial crimes, and phishing scams.
Malware silently steals login data and sends it to hackers. Changing passwords is useless in the presence of malware and infostealers. Installing antivirus software helps detect and remove malware from smartphones and computers completely.
An October report by Security[dot]org found that about 66% of U.S. adults used antivirus software in 2025. Many users have unprotected devices that are vulnerable to infostealer malware. The report stated that $16.6 billion was lost to cybercrime in a single year.
If someone thinks their device has malware, they should act right away.
 cryptopolitan.com
cryptopolitan.com
