Leading crypto transaction platform, Transak, has confirmed a recent security attack that affected 1.14% of its user base i.e., 92,554 users, however no financial data has been compromised, reassured the firm. The security breach, discovered following a sophisticated phishing attack, involved unauthorized access to a third-party KYC vendor’s system through compromised credentials from a Transak employee’s laptop.
The attacker gained access to specific user information, including names, dates of birth, ID documents, and selfies. However, the crypto platform has assured users that no financially sensitive information—such as passwords, credit card details, Social Security Numbers, or phone numbers—was compromised. The attackers have gained around 300GB of data involving data from one million users across Transak’s clients including Metamask, Trust wallet, Zil Swap and others.
In an official statement, Transak said, “Transak operates as a fully non-custodial platform, meaning that user funds—whether fiat or cryptocurrency—are never held by us and therefore remain completely secure and unaffected by any such attack.”
The problems and issues associated with third parties in the Web3 space are not eliminated until we find a nonprofit solution.
Well done, @TransakThanks @zachxbt for the coverage in your Telegram channel pic.twitter.com/90dBJOOLS6
— Felix500 (@FreedomToType) October 21, 2024
Transak informed that upon identifying the breach, the team immediately initiated an investigation with top cybersecurity firms and forensic experts, halting any further unauthorized access. The company is also contacting affected users and partners, while working to improve employee training and system protections to prevent future attacks. Authorities including the UK’s Information Commissioner’s Office (ICO) have been notified, and the company is cooperating with regulators across the EU and US.
The hackers have also put out a message saying that:
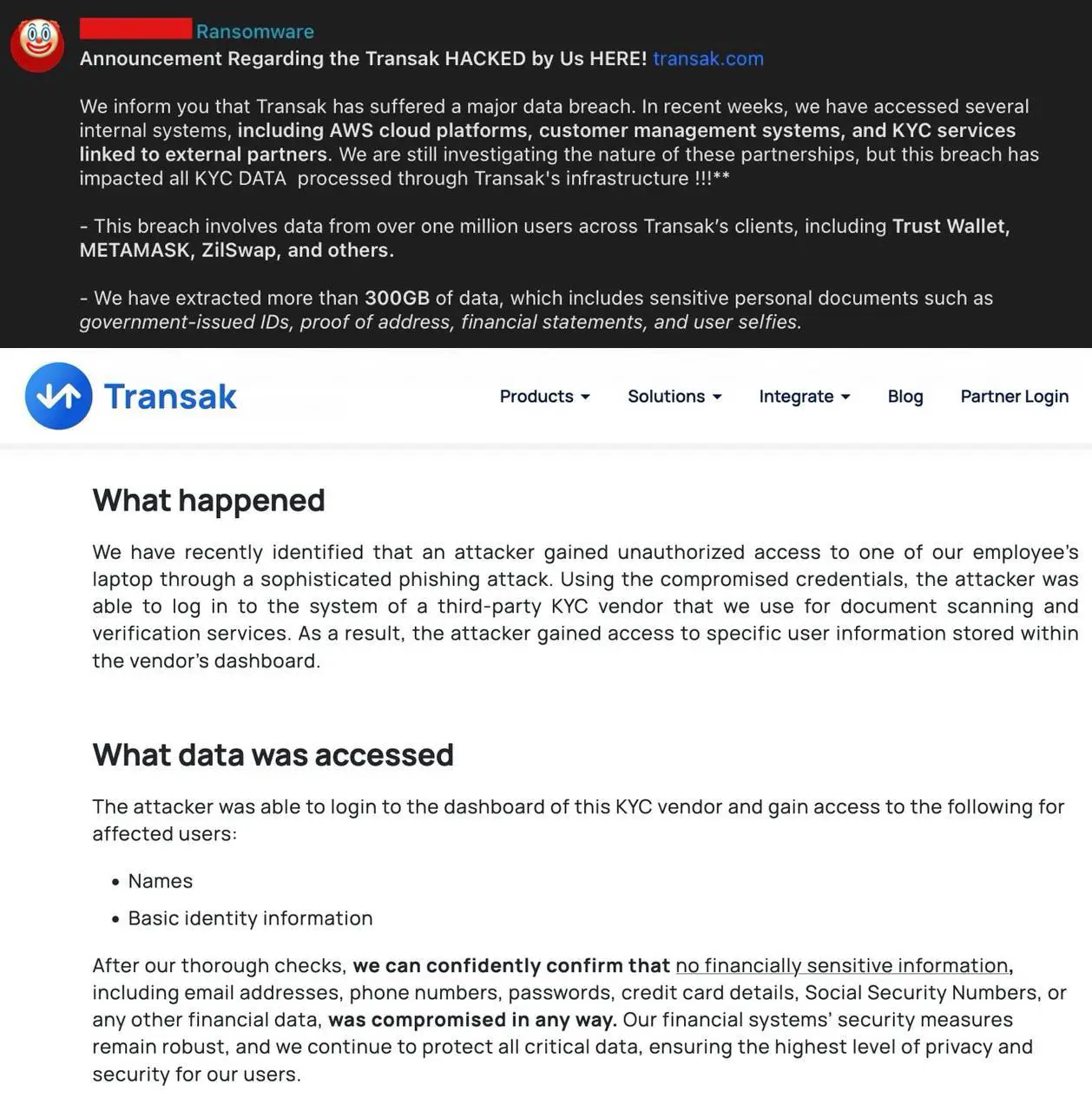
Even so, there is no indication that the data has been misused, Transak has advised affected users to remain vigilant and monitor for suspicious activity.
 cryptonewsz.com
cryptonewsz.com
