The Onyx lending and borrowing platform has been exploited for $3.8M. Hacken, the security auditing hub, analyzed the unusual activity on the platform and estimated the nature of the attack.
Onyx Protocol has been affected by an exploit, losing $3.8M. The attack was achieved via a custom-generated malicious contract, deployed just minutes before calling to Onyx. The hacker managed to drain Virtual USD (VUSD), the protocol’s native stablecoin. This is the second hack for Onyx since November 3, 2023, when the TVL of the project also crashed. The exploit led to additional social media attacks, with faked links claiming to safeguard assets. The best approach is to only interact with the official social media of Onyx Protocol.
Onyx announced that VUSD itself is not affected and will continue to function. However, the exploit ended up destroying the stablecoin’s peg, despite the extra collateral. VUSD crashed to a low of $0.39 and did not recover its $1 nominal level immediately.
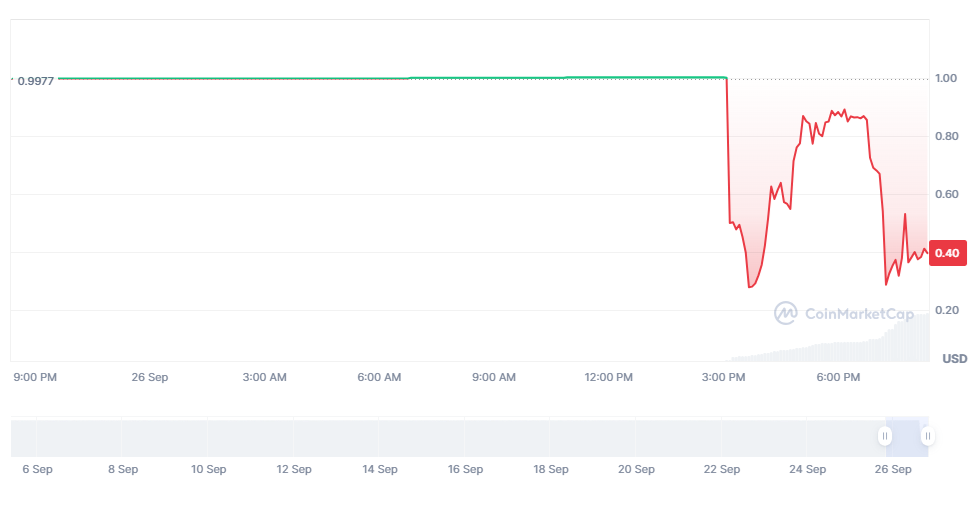
While the final sum that the hacker managed to withdraw is small, the protocol’s losses may be deeper. The VUSD token has a nominal circulating supply above $51M, but its current market capitalization is at $19M.
Onyx faced precision exploit of its exchange rate
One of the reasons for the Onyx exploit was the availability of low-liquidity pools. Analysis by Hacken estimated the exploit was due to an exchange rate miscalculation, when there is low liquidity in some pairs. The hacker prepared a smart contract to swap WETH for Onyx $ETH (oETH).
Starting with a 2,000 WETH loan from Balancer, the hacker moved through several crypto assets. At the same time, the malicious contract spammed Onyx with a series of low-value $ETH transactions. The result of the swaps and pool transfers netted the hacker with 3.8M VUSD, nominally valued at $3.8M.
The final transaction managed to withdraw 300K VUSD, which were swapped for $ETH using CoW Protocol split trades. The transactions caused some slippage and the VUSD price was lower than the $1 nominal, so one of the outgoing transactions was for $191K.
Other assets from Onyx also affected
The series of attacks against Onyx pools affected several assets. Peckshield identified transfers of 4.1m VUSD, 7.35m Onyxcoin ($XCN), 5k $DAI, 0.23 WBTC, 50k $USDT. All of the transfers happened in one transaction, carried out by the malicious smart contract.
Onyx is a Compound V2 hard fork, carrying all the flaws of the protocol. Onyx itself has been hacked before in a similar way, exploiting value calculations and the exchange rate on illiquid pairs.
Sonne Protocol was exploited in May, again due to known flaws on Compound V2, which affected all forked projects and have not been repaired. The flaw is seen whenever the protocol initiates new, unfunded markets. The introduction of new pairs in a dynamic DeFi space has multiplied the problem, leading to several hacks.
Due to the miscalculation, the hacker could call the protocol’s smart contract and receive much bigger loans in exchange for negligible collateral.
The current Onyx attack has a similar structure to the Sonne Protocol hack, again withdrawing a substantial amount of tokens for minimal collateral. The long series of 56 spam transactions whittled away at the Onyx exchange rate, again allowing the hacker to withdraw all funds for a tiny collateral.
So far, no NFTs have been affected. Onyx Protocol hosts Bored Ape (BAYC) and Mutated Ape (MAYC) $NFT for up to 37% annualized passive income. PeckShield also detected a flaw with the project’s $NFT contract, though this has not led to an additional exploit.
The attack may be the work of a rogue employee
The Onyx protocol attack is relatively small, even compared to individual wallet attacks. The effect on the value of VUSD and other assets may be bigger. But the attack may be exposing another serious threat to crypto projects – rogue employees.
The Onyx protocol exploit may be due to a North Korean hacker posing as a project developer. Researchers claim they have contacted the Onyx team with potential evidence of ties to DRPK hackers.
On the other hand, the Compound V2 vulnerability is well-known, and may not have required insider knowledge to exploit.
Cryptopolitan reporting by Hristina Vasileva
 cryptopolitan.com
cryptopolitan.com
