The crypto community has heavily criticized blockchain security firm CertiK for its issues with the crypto exchange Kraken. On June 19, the company revealed itself as the ‘security research’ company Kraken had attributed a theft worth $3 million worth of digital assets to.
Kraken’s chief security officer Nick Percoco had revealed that an unnamed “security researcher” had exploited a bug on the crypto exchange to steal millions in digital assets. Percoco continued that the researcher had refused to return the stolen funds and instead chose to extort the exchange for a speculative amount.
Kraken recovers stolen funds
A few hours after Kraken’s revelation, CertiK stated that it had informed Kraken of the exploit that allowed it to withdraw the funds from the exchange’s accounts. The security firm posted a timeline of the events and claimed that Kraken threatened its employees. It stated:
“After initial successful conversations on identifying and fixing the vulnerability, Kraken’s security operation team has THREATENED individual CertiK employees to repay a MISMATCHED amount of crypto in an UNREASONABLE time even WITHOUT providing repayment addresses.”
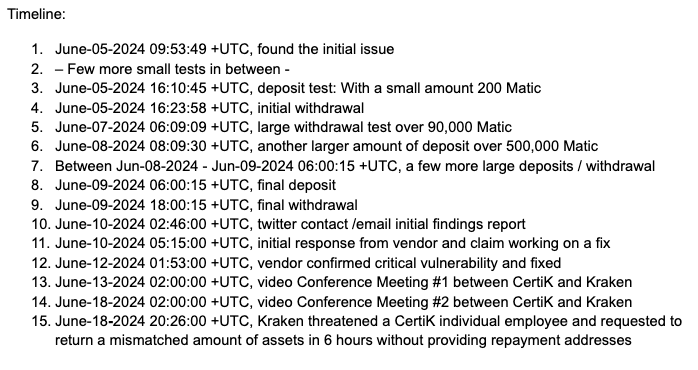
Nevertheless, CertiK revealed that it would transfer the “stolen” funds to an account that Kraken can access. By June 20, Percoco confirmed that Kraken had received all the funds, less the transaction fees.
CertiK’s actions attract criticism
While Kraken would be celebrating fixing a critical bug and recovering funds, CertiK is now facing a barrage of criticism from the crypto community for its role in the events. Taylor Monahan, a crypto security expert, questioned why the blockchain security firm performed more than one test transaction to prove the existence of the vulnerability.
Furthermore, the community questioned CertiK’s motive in moving some of the Kraken funds through the OFAC-sanctioned crypto mixer Tornado Cash and its use of ChangeNOW, a non-custodial crypto exchange with lax know-your-customers processes.
However, CertiK insists that it made the right decision. The firm noted that its test lasted for five days and was on such a grand scale because it was trying to discover how weak the Kraken security system was. It stated:
“The real question should be why Kraken’s in-depth defense system failed to detect so many test transactions. This is indeed what we were testing. You often heard from a weak exchange’s response to a security bug finding with a brag of their strong risk control and in-depth defense system (that they claim would prevent any significant loss). CertiK put this to the test with Kraken, and they failed miserably.”
It also denied ever asking for a bounty and claimed it consistently assured Kraken of its plan to return the funds.
Cryptopolitan reporting by Oluwapelumi Adejumo
 cryptopolitan.com
cryptopolitan.com