The first quarter of 2024 has unfolded as a pivotal chapter in the narrative of Web3 security, marked by both notable achievements in threat mitigation and profound challenges.
This report synthesizes key findings from AI Web3 security firm Cyvers’ comprehensive analysis of security incidents in Q1 2024, highlighting emerging threats and underscoring the importance of resilience within the ecosystem.
Executive Summary
Amid the continuous advancement of DeFi, DePIN (Decentralized Physical Infrastructure Networks), RWAs (Real World Assets), and other blockchain-based applications, we’ve observed a corresponding escalation in sophisticated security threats. Attack vectors have diversified, with code vulnerabilities leading to substantial financial repercussions and access control breaches proving exceptionally costly.
These trends signal an urgent need for enhanced security measures and greater vigilance within the Web3 community.
Cyvers, in partnership with BeInCrypto, has demonstrated its commitment to this cause by pioneering real-time threat detection and AI-driven security solutions. The goal is to provide rapid and precise identification of threats, offering proactive mitigation and safeguarding assets across the blockchain.
These threats deploy a range of attack vectors—from smart contract vulnerabilities to phishing scams—aiming to exploit the open and interconnected nature of Web3 technologies. In response to these challenges, the Web3 community has rallied, emphasizing the importance of security as a foundational element of the ecosystem’s infrastructure.
Key Security Trends and Statistics
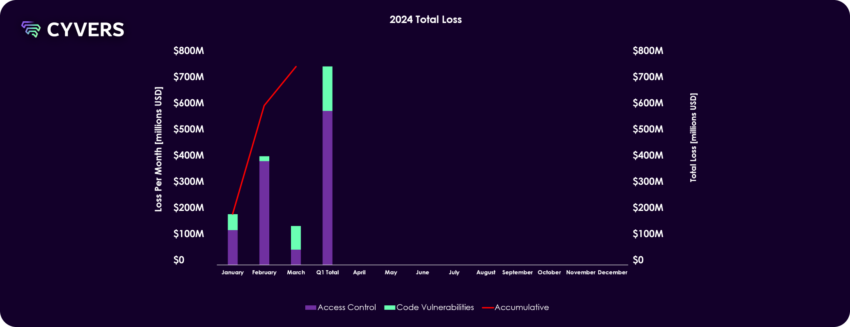
The Total Stolen Value (TSV) in the first quarter of 2024 is approximately $739.7 million. January witnessed the highest number of attacks (27), followed by March (21), and February (18). Despite having the least number of attacks, February had a high financial impact, with around $405.3 million lost to attacks.
The average loss per attack calculated to be approximately $6.7 million, indicating the high stakes involved in Web3 security.
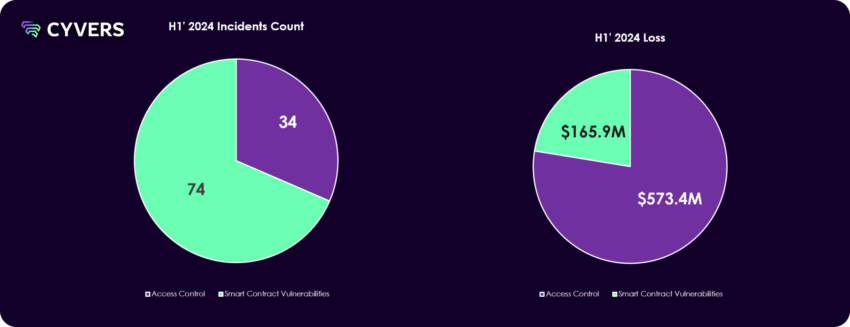
The most common attack vector was Code Vulnerabilities, with 37 instances, resulting in a loss of about $165.9 million. Though less prevalent, Access Control attacks were far more costly, resulting in a loss of about $573.8 million.
There were 10 instances where hacks were exclusively detected by Cyvers, which underlines the importance of proactive security measures, sophisticated algorithms, and continuous optimization.
Three of these instances were among the Top 10 Hacks of Q1 2024.
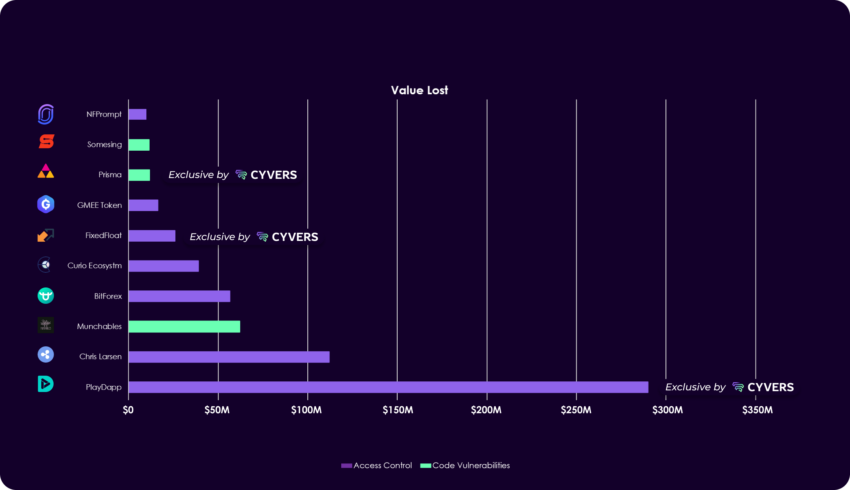
PlayDapp’s Security Breach Analysis
In February 2024, prominent gaming and NFT platform PlayDapp faced a severe security challenge when it suffered two consecutive exploits leading to an unprecedented minting of PLA tokens. Initially, on February 9, an unauthorized entity minted 200 million PLA tokens, valued at roughly $36.5 million.
A few days later, on February 12, the same entity reportedly minted an additional 1.79 billion PLA tokens, equating to a staggering $253.9 million. These exploits collectively resulted in a total loss of about $290 million.
The primary cause of the breach was identified as a smart contract vulnerability, which allowed the attacker to mint tokens without the necessary authority. The repercussions were immediate and severe, as the market price for PLA tokens plummeted due to the sudden influx of unauthorized tokens. PlayDapp’s team attempted to negotiate with the attacker, offering a $1 million bounty for the return of the stolen funds, but to no avail.
The security measures taken post-incident included the pausing of the PLA smart contract and the initiation of a contract migration based on pre-exploit snapshots of holder balances. PlayDapp’s prompt response to pause the contract and engage with law enforcement and blockchain forensic firms demonstrated a commitment to security and transparency. The efforts to liaise with exchanges and track the stolen funds were ongoing, with strategies to mitigate the impact and prevent such incidents in the future being actively discussed.
The PlayDapp incident serves as a cautionary tale about the vulnerabilities inherent in smart contracts, particularly regarding the minting and management of tokens. Indeed, the lessons from the PlayDapp incident are manifold: the absolute necessity of continual security vigilance, the importance of proactive and reactive security measures, and the ever-present need for community education on security best practices.
Regulatory Changes on Web3 Security
In Q1 2024, the global digital asset landscape saw notable regulatory advancements which have had a considerable impact on Web3 security.
PwC’s Global Crypto Regulatory Report emphasizes the ongoing evolution in digital asset regulation, suggesting that while substantial progress was made in 2023, the industry continues to face a significant regulatory workload. Such developments are crucial as they provide a structured framework for operations, enhance global regulatory policies, and help establish global prudential standards, potentially influencing the EU’s Markets in Crypto-Assets regulation and other international policies.
Moreover, after the high-profile collapse of FTX, regulatory bodies have been prompted to take a more stringent approach to digital asset rules to better protect the investing public. The US Securities and Exchange Commission (SEC), for instance, had planned to release new rules governing digital asset exchanges and offerings. These rules were expected to provide comprehensive regulations for digital asset offerings, alongside guidelines for digital asset exchanges.
This response to past events demonstrates a clear intent by regulatory bodies to improve oversight and prevent similar occurrences in the future.
These regulations aim not only to safeguard investors but also to ensure the orderly functioning of digital asset markets. For Cyvers, these developments could serve as an opportunity to contribute to regulatory discussions, leveraging its expertise to guide the formulation of policies that balance the need for security with the potential for innovation in the Web3 space.
As regulations evolve, Cyvers and BeInCrypto’s ability to provide compliance-aligned security services becomes ever more critical. Q1 2024 has therefore been a pivotal time for Web3 security, marked by regulatory bodies around the world taking lessons from past events to fortify the industry’s defenses and establish a secure foundation for the burgeoning digital economy.
Recommendations for Enhancing Web3 Security
In the pursuit of a fortified Web3 landscape, Cyvers explained to BeInCrypto strategic ways to enhance security postures for various stakeholders within the ecosystem:
For Projects:
- Smart Contract Auditing: Ensure that smart contracts undergo thorough securityaudits by reputable firms. Regularly re-audit after major updates or changes in thecontract’s logic. Check out our recommended auditors here.
- Incident Response Planning: Develop an incident response plan tailored to potentialWeb3-specific breaches, detailing immediate actions, communication protocols, andcontingency measures.
- Security Modules Integration: Implement real-time threat detection and securitymodules, like those provided by Cyvers, to continually monitor and protect against malicious activity.
For Developers:
- Security-First Design: Embrace a security-first approach when designing systems,prioritizing security in every phase of development.
- Continuous Education: Stay informed about the latest security research,vulnerabilities, and protection strategies. Engage with the community to shareknowledge and best practices.
- Decentralization of Control: Avoid single points of failure in your systems. Use multi-signature wallets and distributed decision-making for critical operations.
For Investors:
- Due Diligence: Exercise due diligence by reviewing the security practices of projectsbefore investing. Check for audit reports, security affiliations, and incident histories.
- Diversify Holdings: Protect your portfolio from targeted breaches by diversifyingyour holdings across various platforms and wallets.
- Use Trusted Platforms: Engage with platforms that have a proven track record ofsecurity and that implement the latest security measures.
For Users:
- Secure Wallet Practices: Utilize hardware wallets for significant holdings, practicesafe storage of private keys, and employ multi-factor authentication.
- Beware of Phishing: Educate yourself on common phishing tactics within the Web3 space. Verify URLs, double-check smart contract interactions, and be cautious withunsolicited requests.
- Stay Updated: Regularly update your software to the latest versions, ensuring that security patches are applied.
By adhering to these recommendations, stakeholders across the Web3 ecosystem can significantly reduce their risk profile and contribute to creating a secure and resilient digital environment. It is through collective vigilance and proactive measures that we can navigate the Web3 ecosystem with safety and confidence.
 beincrypto.com
beincrypto.com