Cross-chain yield protocol Mozaic Finance suffered an exploit on Mar. 15, resulting in a loss of $2,012,789. Security firm CertiK reported that the vaults were compromised through a function named ‘bridgeViaLifi,’ which indicates a private key compromise (PKC) as it required authorization from the Master role, which is typically reserved for the most privileged entity within the contract’s hierarchy.
After snagging over $2 million, the exploiters deposited the funds into the crypto exchange MEXC. Mozaic announced the exploit on an X post and two hours later published a link for their refunding initiative for affected users, who were able to recover their funds by checking their wallets’ eligibility.
“In light of the recent exploit, we are committed to fully compensating affected users. Our plan includes immediate steps for security enhancements and detailed compensation procedures. We appreciate your patience and trust as we work to resolve this issue,” Mozaic stated on its refund page.
Exploits via PKC were the most harmful in 2023, with over $882 million stolen through those attack vectors, according to CertiK’s “Hack3d: The Web3 Security Report.”
Joe Green, Head of the Quick Response Team at CertiK, shared that 21 incidents involving PKC occurred in 2024, with losses exceeding $230 million. This already represents 26% of all the amount stolen last year.
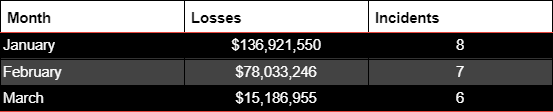
“Unfortunately, it is likely that private key compromises will continue to be a major driver for losses throughout 2024. Last year we saw ~$882m lost to private key compromises and we’re already at ~$230m this year (according to our most up to date information),” Green concluded.
 cryptobriefing.com
cryptobriefing.com
