Bitcoin developers largely dismiss quantum computing as a near-term threat to network security, according to an index of public statements compiled by Nic Carter.
Carter’s Index Shows Bitcoin Developers Largely Unmoved by Quantum Computing Warnings
Nic Carter, a general partner at Castle Island Ventures and co-founder of Coin Metrics, assembled comments from Bitcoin developers to assess how seriously they view quantum risks compared with claims circulating in broader crypto discussions. His compilation suggests that most developers see quantum-related concerns as speculative rather than imminent.
The index published to Substack draws from forum posts, mailing lists, and public discussions in which developers responded to questions about whether advances in quantum computing could compromise Bitcoin’s cryptography. In most cases, developers characterized such scenarios as highly theoretical, emphasizing the absence of practical quantum machines capable of breaking elliptic curve cryptography at scale.
Carter has been flagging quantum-related risks for an extended period and has argued that Bitcoin developers are effectively “Sleepwalking” toward a future quantum reckoning. On Wednesday, he released the index and said on the social media platform X, “ Bitcoin developers are not concerned about quantum risk – with receipts.” He further added:
My piece profiles the attitudes of about 40 different Bitcoin developers in their own words, if you disagree with how I’ve characterized your view shoot me a DM or email and I’ll update it.
Several developers cited the long timelines typically associated with quantum breakthroughs, arguing that even meaningful progress would likely be gradual and publicly visible. That visibility, they said, would give the network time to respond through standard upgrade processes rather than emergency interventions.
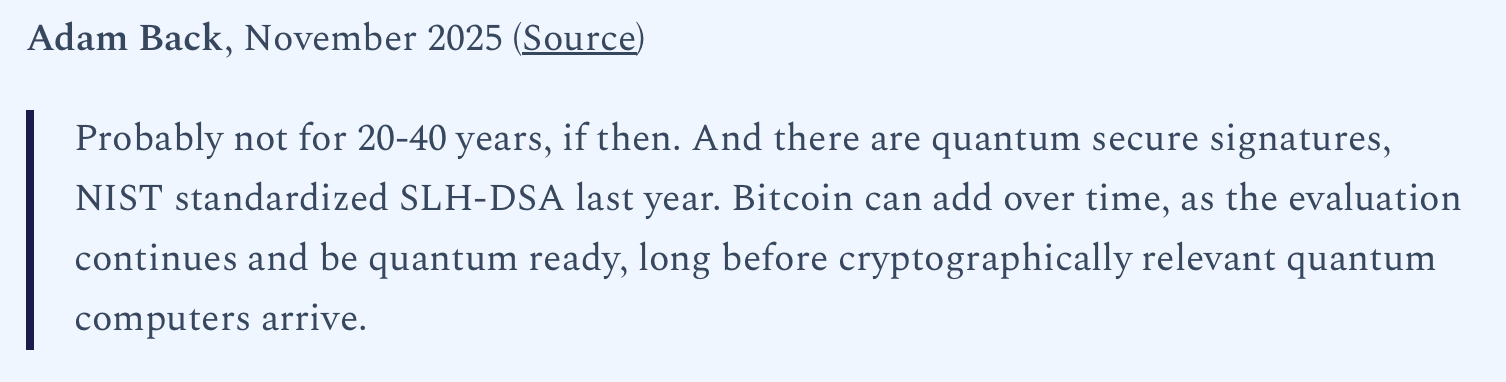
Critics of this stance argue that Bitcoin’s decentralized governance model could slow reaction times if a genuine quantum threat emerges. They point out that Bitcoin relies on a relatively small group of contributors to propose and review changes, raising concerns about whether the network could coordinate quickly enough under pressure.

Some researchers and commentators have warned that quantum computers could eventually derive private keys from exposed public keys, potentially allowing attackers to spend coins without authorization. These warnings often cite dormant or reused addresses as hypothetical points of vulnerability if cryptographic assumptions were to fail.

Carter’s compilation shows that many developers push back on these claims, noting that Bitcoin already minimizes key exposure by default and that users can further reduce risk through best practices. Developers also emphasized that theoretical vulnerabilities do not automatically translate into real-world exploitability.
The discussion has also touched on potential protocol upgrades, including proposals such as BIP360, which would introduce quantum-resistant cryptographic schemes. While some developers view such proposals as prudent long-term research, Carter’s index indicates that most do not see an immediate need to prioritize them.
Developers referenced in the index often stressed trade-offs involved in major cryptographic changes, including increased transaction sizes, performance considerations, and compatibility with existing infrastructure. These costs, they argued, should be weighed against realistic threat models rather than speculative scenarios.
The debate reflects a broader tension within Bitcoin’s development culture, which historically favors conservative changes and extensive peer review. From this perspective, the absence of urgency around quantum risks aligns with Bitcoin’s incremental approach to protocol evolution.
Also read: Wintermute Founder Casts a Cold Eye on Crypto’s Direction
Carter framed the index as an observational snapshot rather than an endorsement of any position, highlighting the gap between public anxiety about quantum computing and the views expressed by those maintaining the software. He noted that the compilation is intended to inform discussion, not settle it.
As quantum research continues to advance, the question of when, or whether, Bitcoin should adopt quantum-resistant cryptography remains unresolved. For now, Carter’s findings suggest that most developers believe existing safeguards and long timelines leave room for measured responses rather than immediate action.
FAQ ❓
-
What did Nic Carter analyze?
Carter compiled public statements from Bitcoin developers addressing quantum computing risks to the network. -
Are Bitcoin developers worried about quantum attacks?
Most developers cited in the index view quantum threats as theoretical and not an immediate concern. -
Could Bitcoin upgrade to resist quantum computing?
Proposals such as BIP360 exist, but developers generally see them as long-term research rather than urgent fixes. -
Who is Nic Carter?
Carter is a general partner at Castle Island Ventures and a co-founder of Coin Metrics.
 news.bitcoin.com
news.bitcoin.com
