The fake Skype application is being heavily distributed on the Chinese internet, the SlowMist Security Team has learned.
As many international marketplaces are inaccessible within China due to local regulations, bad actors are actively exploiting this gap, flooding the market with phishing applications targeting crypto investors.
According to a blockchain security firm SlowMist, a group of Chinese scammers has recently started distributing a fake version of Skype — version 8.87.0.403 — for Android devices among multiple local marketplaces, such as 51pgzs, siyuetian, and others. They lure victims to believe they downloaded a legit version of the video chat application.
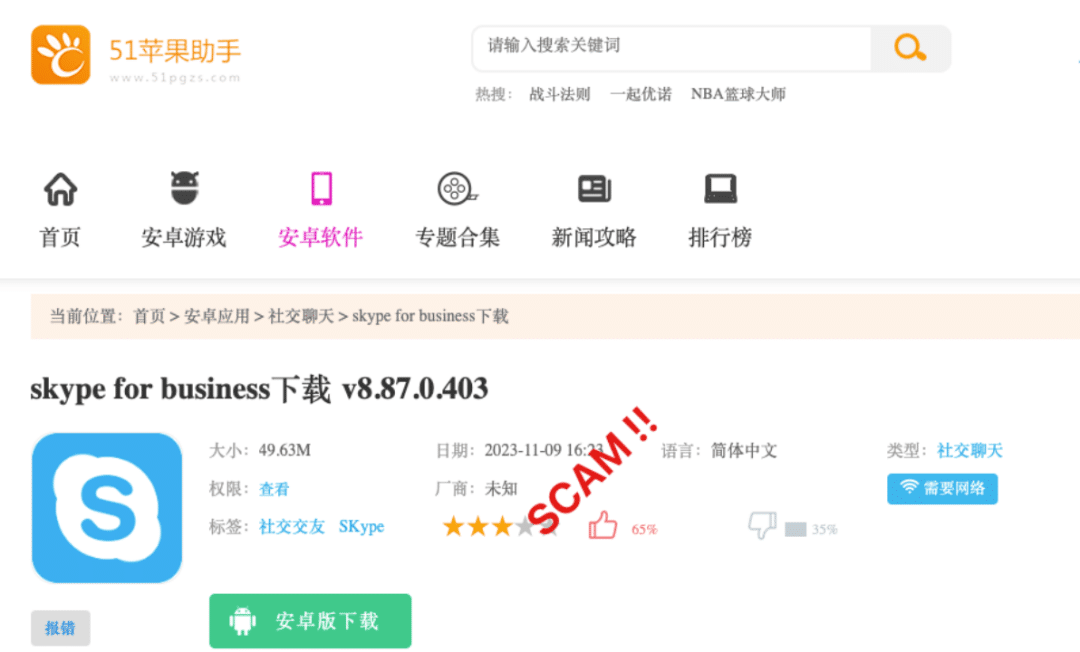
Once the malicious application is installed, it obtains images from various directories on the Android phone and monitors in real-time for any new images. All the images stored on the victim’s device are then uploaded to the phishing gang’s backend interface.
You might also like: North Korea targets blockchain engineers with new macOS malware
Analysts at SlowMist also learned that the gang behind the fake Skype application also targeted users in 2022 with its scam version of Binance, pointing out that both malicious applications have similar backend domain “bn-download3[dot]com.”
“Further analysis revealed that ‘bn-download[number]’ is a series of fake domains used by this phishing gang specifically for Binance phishing, indicating that this gang is a repeat offender targeting Web3 specifically.”
SlowMist
In addition to images, the malicious application sends data to bad actors’ backend, such as device information, user ID, and phone number. To make things worse, the fake Skype even monitors incoming and outgoing messages to see if they include TRON or Ethereum-type address format strings to replace them with addresses pre-made by the scammers automatically.
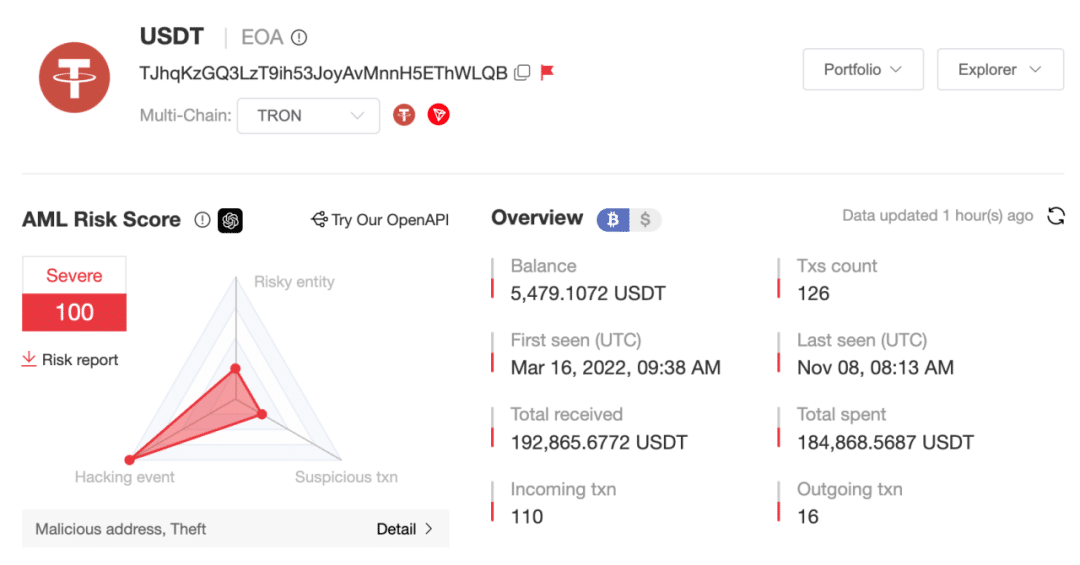
SlowMist found out that the TRON chain address, which belongs to the scammers, had received nearly $193,000 in Tether (USDT) with 110 transactions, noting that funds are still coming in as the most recent transaction was on Nov 8, 2023. In general, most of the stolen funds were laundered through BitKeep’s Swap service, with the transaction fees covered by a user registered on the OKX crypto exchange, SlowMist emphasized.
Read more: Blackberry identifies malware that affects crypto community
