The US and Chinese National Databases Withhold Vulnerability Information. Decentralized Database Can Deal With It
Tae-Jin (TJ) Kang is a technology industry executive and entrepreneur. He is the CEO of Secure Planet. In addition to founding a number of successful technology startups, Mr. Kang has held senior management positions with global technology leaders that include Korea Telecom and Samsung Electronics. Tae-Jin Kang has exclusively contributed an article to Bitnewstoday.com. The first part presented the obvious cybersecurity problems to deal with. This is the second part of the article, which finds the underlying issues and discovers the solutions.
Information Manipulation and Withholding Cause Cybersecurity Issues
Beyond the issue of timeliness, there are open questions about whether the authorities maintaining these databases are motivated to freely share all the information that they collect. The National Security Agency (NSA), in particular, has been known with keeping vulnerabilities secrets for espionage purposes, rather than disclosing them. This prevents the relevant system and device manufacturers from addressing their problems to protect the greater public. The Vulnerabilities Equities Policy allows the federal government to justify temporarily retaining knowledge of vulnerabilities to use for “national security and law enforcement purposes, such as intelligence collection, military operations and/or counterintelligence.”
The U.S. government is not the only nation-state known to conceal or tamper with the vulnerability data. The CNNVD also displays signs of government-related data manipulation. Managed by China’s intelligence community and housed by the Ministry of State Security (MSS), the CNNVD has backdated original publication dates of vulnerabilities in an attempt to conceal which vulnerabilities the MSS may itself leverage. These actions also prevent researchers from predicting Chinese advanced persistent threat behavior. According to a Recorded Future report, by eliminating the publication lag of these security risks, the Chinese government attempts to hide the fact that they withhold a selection of high-threat vulnerabilities that could be employed to advance national security goals.

(Recorded Future)
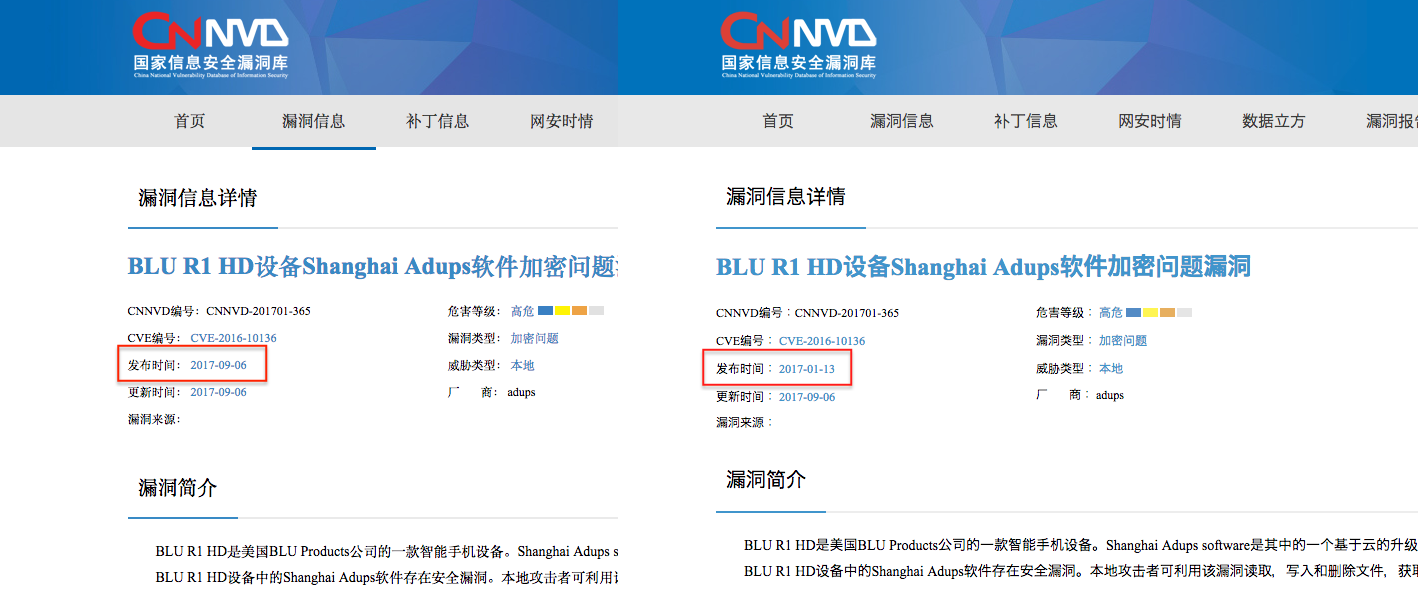
On the left is a screenshot of CNNVD’s website taken on October 23, 2017, containing information about vulnerabilities detected in software from Shanghai Adups Technology Company. The original publication date reads September 6, 2017. However, the right screenshot of the same page shows a different publication date - January 13, 2017, a backdating of 236 days. This manipulation is particularly problematic when considering that this software was deployed in cheap phones to secretly siphon off user data without disclosure or consent.
Clearly, security-conscious organizations cannot rely on nation-state-sponsored entities to efficiently and freely share the information needed to mitigate cyber-attacks. It has thus become vital to create a more timely and transparent system for creating and maintaining vulnerabilities databases.
Using Blockchain and Cryptocurrency Platform to Address These Issues
We must develop a new, secure model that is committed to the free flow of information about vulnerabilities, so we can address known security threats as quickly and efficiently as possible.
This new approach resolves the issues of the current model by doing the following:
-
Building a decentralized database of OSS vulnerabilities managed by multiple, independent entities with an inherent system of checks and balances to assure a free flow of information;
-
Securing this database with blockchain technology to prevent data manipulation and ensure participants are in-sync;
-
Incentivizing and crowdsourcing users and OSS communities to identify and verify vulnerabilities, thereby increasing both the number of contributors and their participation in as-yet-underserved segments of the OSS market; and
-
Creating an independent economic system which sustainably pays for the operation of the platform.
Blockchain-based Vulnerability Information Platform
The first step in creating this new, open model would be to build a vulnerability database that is operated and maintained by a decentralized, global group of interconnected autonomous stakeholders. These stakeholders would find their motivation in the need for a definitive source of “truth” about vulnerabilities, while their costs to operate and maintain the database would be offset by a token-based system of payment offering access to the entire database.
The new security vulnerability knowledge base would record vulnerability data in blockchain databases that inherently secure the integrity and immutability of the stored information. The combination of independent but interested stakeholders who maintain the database, the usage of blockchain technology to secure the database and an economic model to remunerate the managing stakeholders would create the base for success.
“The More Eyes, The Better To See”
A token system would be used to reward the operators of the nodes participating in vulnerability tracking platform. Tokens would also be used as a “bug bounty” to incentivize and crowdsource the finding and reporting of potential OSS security issues, thereby continuously seeding the database. The smart contract for the bug bounty program would execute when a vulnerability in an OSS project is verified by the OSS community. By activating this incentive system for the general OSS ecosystem, we can counterbalance the currently disproportionate amount of contributor attention given to sponsored and high profile OSS projects. It can encourage participation in OSS projects responsible for software that is widely used but does not have many active contributors – a critical step to secure our IT infrastructure. Tokens could also reward verifiers for correctly validating the reported security vulnerability.
Moreover, by rewarding users with cryptocurrency rather than fiat currency, the vulnerability tracking platform can eliminate currency exchange fees – an important consideration for contributors in developing countries.
Paying for Usage of the New Vulnerability Database
Currently, individuals and organizations can use public databases such as NVD and CNNVD, free of charge. However, the above mentioned deficiencies found in these options may prompt medium and large corporations to purchase access to commercial alternatives, such as VulnDB. Though superior to publicly available versions in their breadth and timeliness of information coverage, commercial databases are often very expensive, and are therefore financially infeasible for smaller companies. Consequently, this new security knowledge base should employ two pricing models. The first option would target large enterprises that plan to check the database on a regular basis as part of their DevOps process. These organizations could pay an upfront fee for unlimited access to the database. The second option would be a pay-as-you-go model designed for smaller companies that do not need to use database as often. Since the new system would run on cryptocurrency, smaller companies would have the option to pay for access to the database by earning tokens through participation in the reporting and verification of security vulnerabilities.
A Better Way Forward
Security breach after security breach, we are constantly reminded of our lack of awareness of OSS security risks and the inadequacies of current centralized vulnerability tracking and mitigation options. These deficiencies, such as time delays, information omission, and uneven attention given across OSS projects, prompt the need to create a more robust and sustainable solution. A new kind of decentralized vulnerability tracking and mitigation system that leverages a cryptocurrency and blockchain technology, appears to be an effective alternative. By building a decentralized, crowdsourced, and comprehensive open source vulnerability database, we can improve and maintain the security of the IT infrastructure on which everyone relies.