Solana wallets have been compromised. SOL holders in self-custody wallets such as Phantom, Slope, Solflare and TrustWallet were urgently advised to revoke all permissions to the wallet and consider transferring the tokens to centralized exchanges (CEX) or cold wallets (where USB is required) such as Ledger including NFTs.
At the time of this writing, hardware wallets (such as Ledger) were not compromised. The nodes temporarily stopped accepting new requests in an effort to slowdown the attack.
Users that had their wallets compromised are advised to complete the following survey to allow engineers from mulitple ecosystems to investigate the exploit:
https://solanafoundation.typeform.com/to/Rxm8STIT
Bybit Suspends SOL Deposits and Withdrawals
Bybit announced it is suspending deposits and withdrawls of assets on the Solana blockchain including SOL:
'Due to the widespread exploit on @solana , #Bybit has taken the steps to temporarily suspend deposit and withdrawal of assets on the Solana blockchain, including $SOL, to protect our clients.
'We will continue to monitor the situation. Thank you for your understanding and support!'
source: Bybit official twitter
The hacker was able to sign the transactions with the users' private keys, which is suggesting a supply chain attack. Both desktop and mobile users that downloaded the wallets' extensions were compromised.
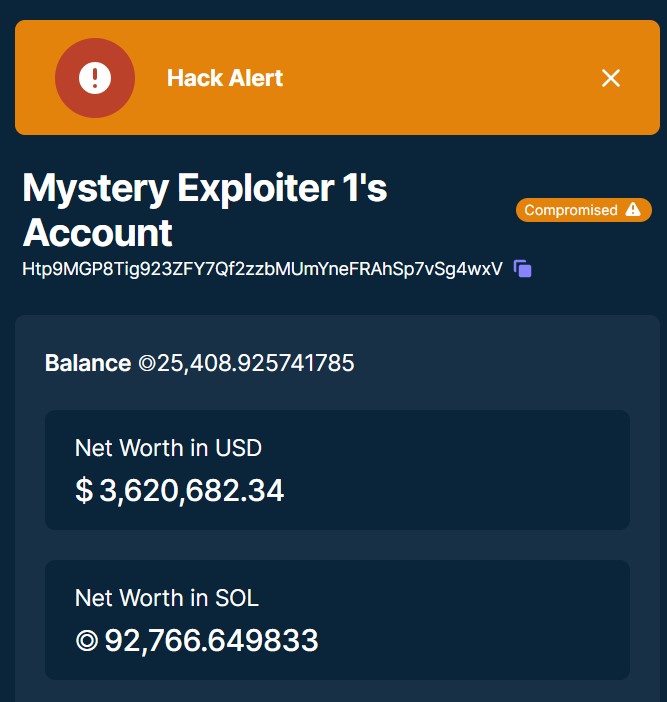
source: solanafm
It has been that at least $8 million were stolen from over 8,000 wallets during the attack using different addresses. The reports that over $500 million were stolen are inaccurate.
There is an illiquid token that only has 30 holders and is highly overvalued (around $560 million).
The following 4 wallets have been linked to attack:
Wallet A
Wallet B
Wallet C
Wallet D
Some of the wallets that have been compromised were inactive for several months.
How were Solana Wallets Hacked?
According to unofficial preliminary findings, "Luca Stealer" may have been behind the attack on Solana. A user on twitter by the name of Matt Dagen outlines how the Luca Stealer may have been inolved in the hack.
The source code for an information-stealing malware coded in Rust was recently released for free on hacking forums. The malware steals stored credit card info, login credentials as well as cookies. It has been suggested the maware was used in the attack.
The malware targets wallet browser addons of both cold and hot wallets including Discord tokens, Steam accounts and more.
The stealer targets a range of "cold" cryptocurrency and "hot" wallet browser addons, Steam accounts, Discord tokens, Ubisoft Play, and more.
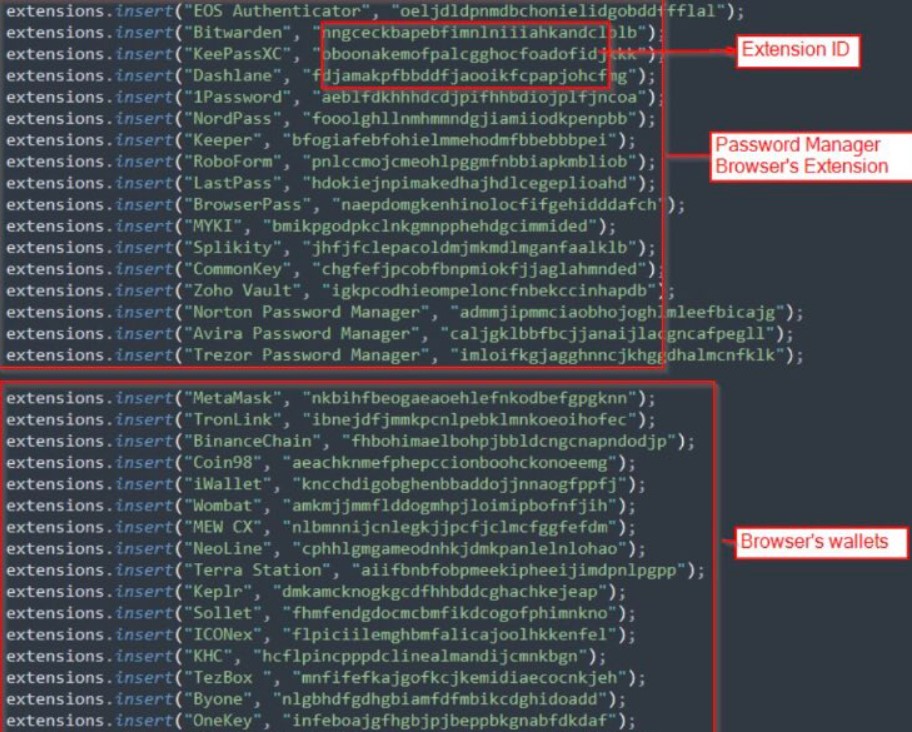
soure: twitter
In addition, Luca also captures screenshots that are saved as a .png file, executes a 'whoami' and send the details to the bad actor.
Luca also captures screenshots and saves them as a .png file, and performs a "whoami" to profile the host system and send the details to its operators.
Although it is not generally found in Luca according to Matt, a clipper is used to modify clipboard contents in order to hijack crypto transactions.
One notable capability typically found in other info-stealers but is not available in Luca is a clipper used to modify clipboard contents to hijack cryptocurrency transactions.
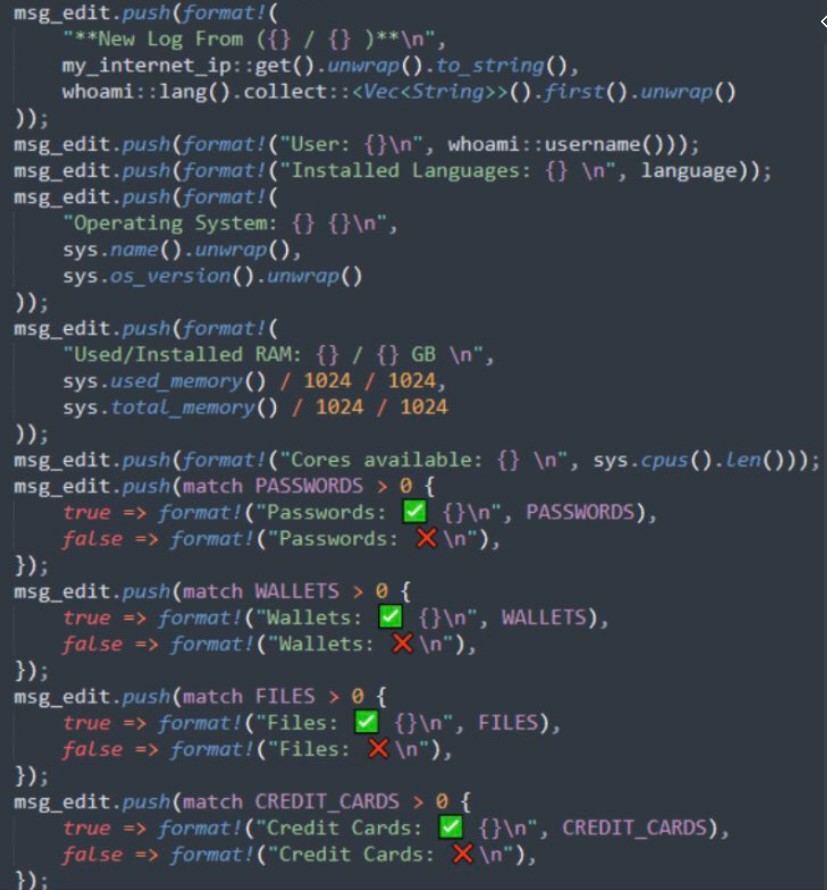
source: twitter
The stolen data is extracted via Discord webhooks and telegram bots (depending if the file exceeds 50MB). The program then uses Discord webhooks to send the data to the bad actor in a ZIP archive.
A summary is provided on the stolen 'loot,' allowing the attacker to estiamte the value of the stolen data.
It is important to highlight these are not the official findings. The exploit is still being investigated.
 financemagnates.com
financemagnates.com