1 Q3 2022 Blockchain Security Overview
A total of 37 major exploits were monitored, with a total loss of approximately $405 million
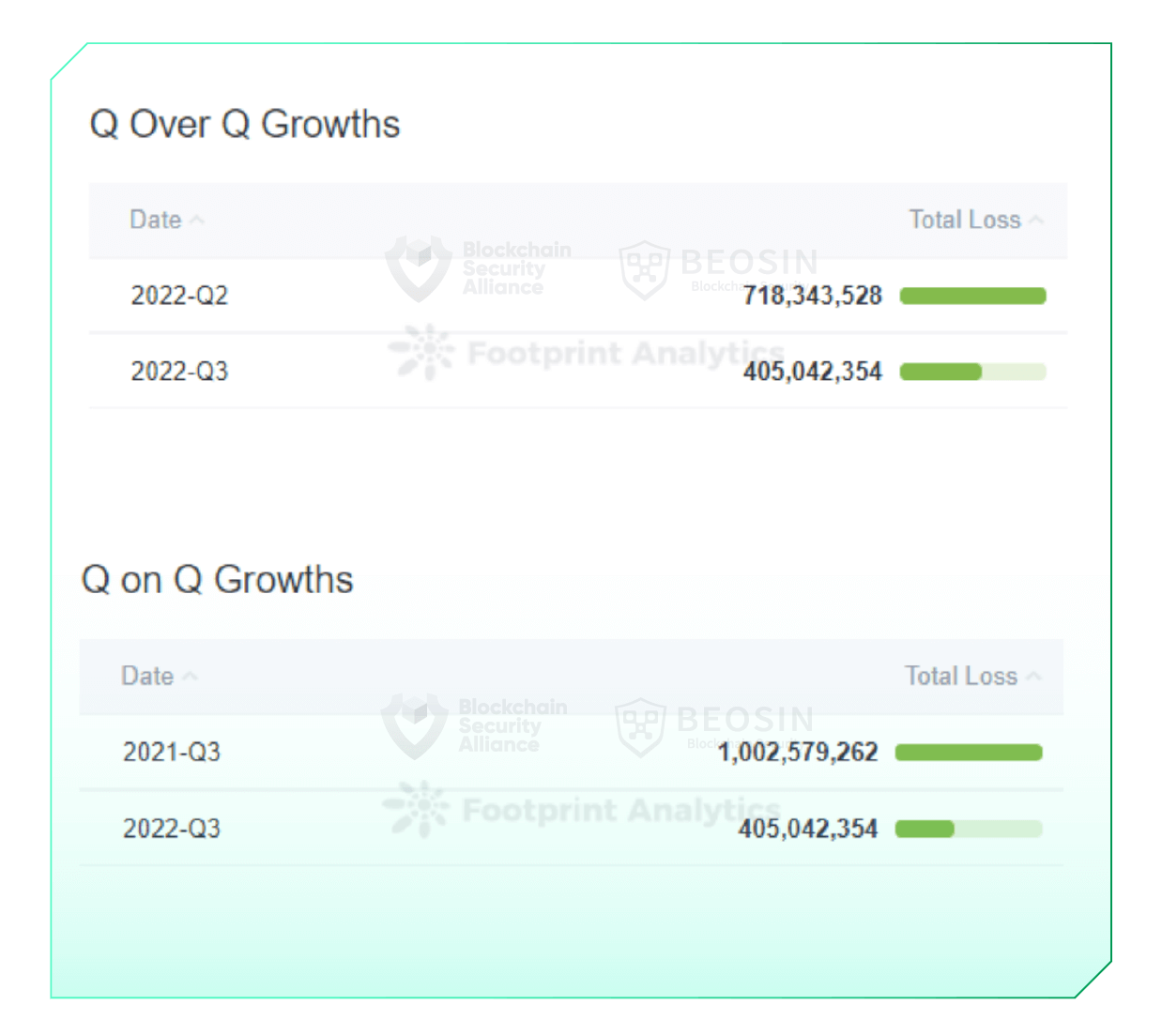
In the third quarter of 2022, Beosin EagleEye monitored over 37 major attacks in the Web3 space, with total losses of approximately $405 million, down approximately 43.6% from $718.34 million in Q2 2022 and a decrease of 59.6% from the loss of $1,002.58 million in Q3 2021.
From January to September 2022, assets lost in the Web3 space due to attacks totaled $2,317.91 million.
In terms of each month, July saw a significant decrease in attacks, making it the least loss amount from attacks since 2022. Hacker activity increased significantly in August and September.
In terms of the project types, 92% of the amount lost came from cross-chain bridges and DeFi protocols. 22 of the 37 attacks occurred in the DeFi space.
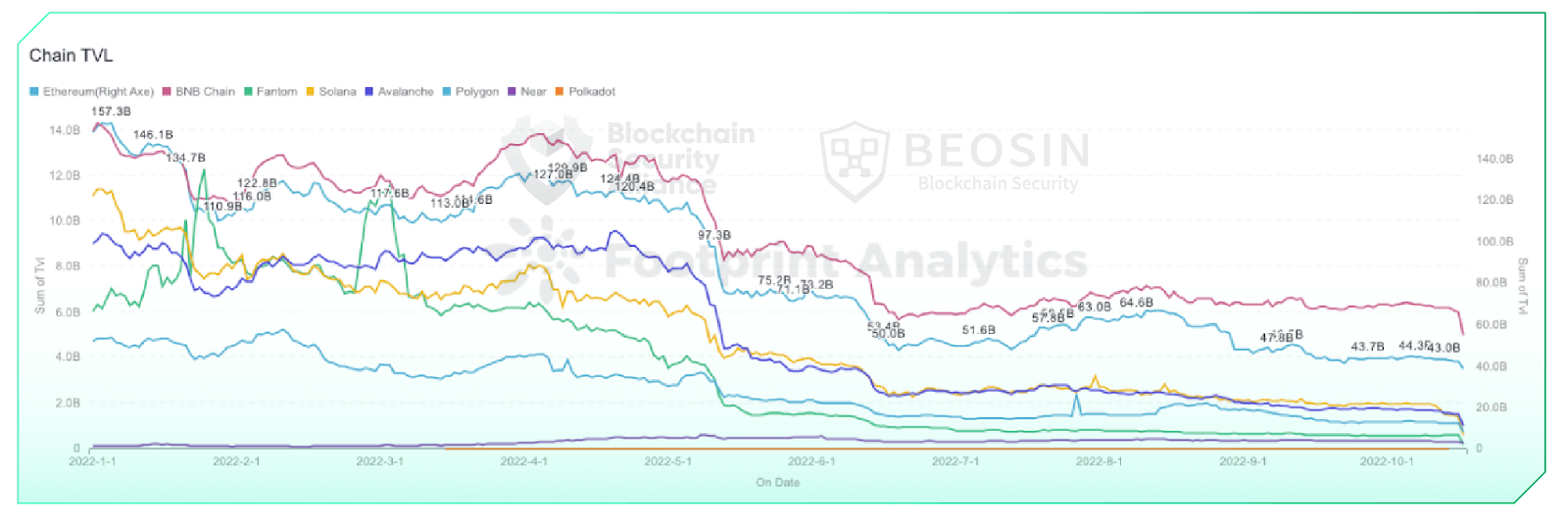
In terms of TVL, after a sharp drop in TVL from May to June, the trend of TVL of each chain tended to be stable this quarter. Late July to early August showed a slight upward trend in TVL, which was also the period with the highest number of attacks and loss amount in this quarter.
In terms of chains, the amount of losses on Ethereum reached $374.28 million this quarter, accounting for 92% of the total losses. The most frequently attacked chain was BNB Chain, which reached 16 times.
In terms of attack types, 92% of the loss amount was caused by contract vulnerability exploits and private key compromises.
In terms of fund flows, about $204.2 million of the stolen funds flowed into Tornado Cash, accounting for about 50.4% of the funds stolen in the quarter. Only about 4% of the stolen funds were recovered during the quarter.
In terms of audits, only 40% of the rekt projects were audited.
2 Overview of exploits
Overall attacks fell in Q3 compared to Q2
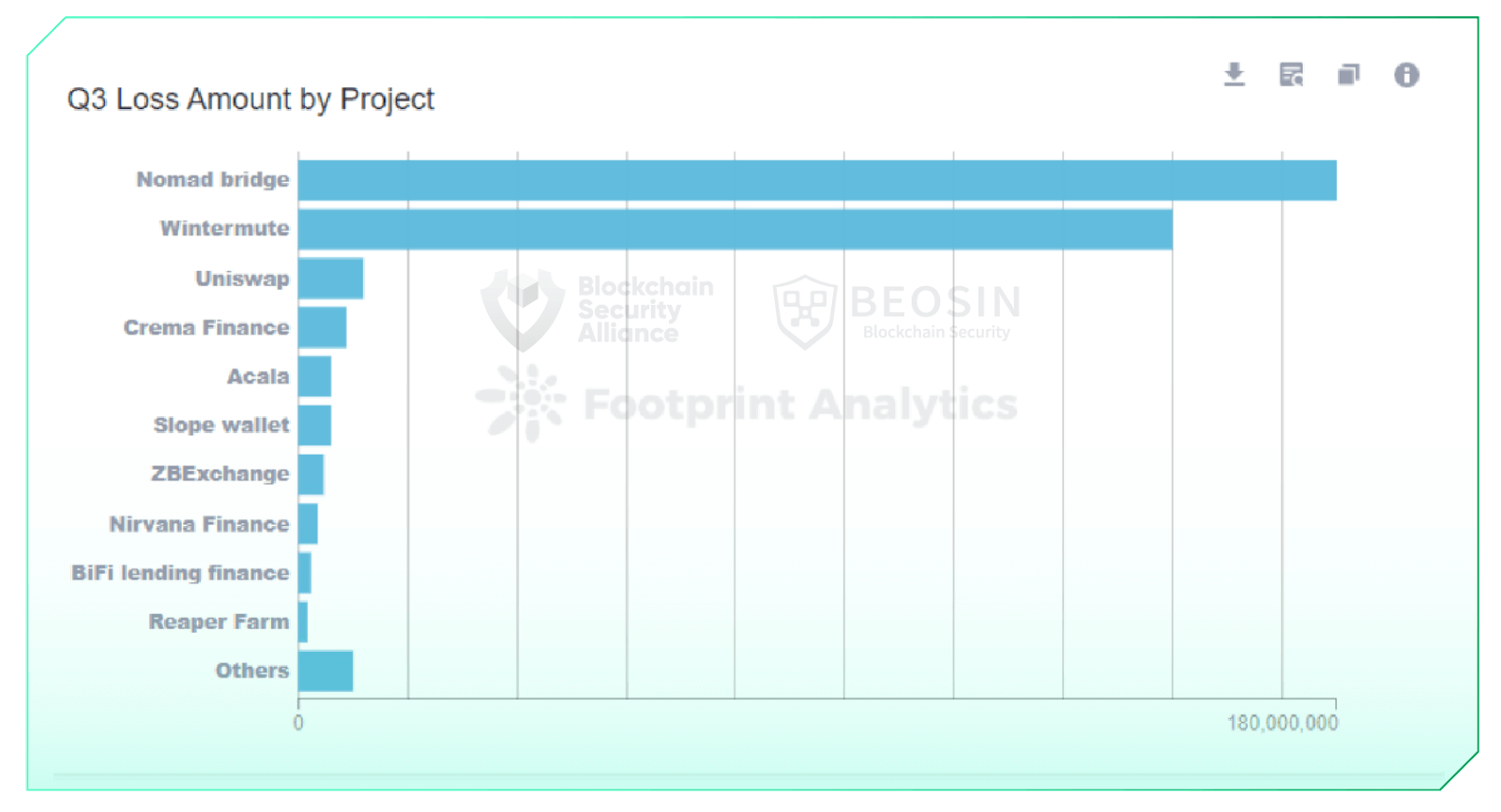
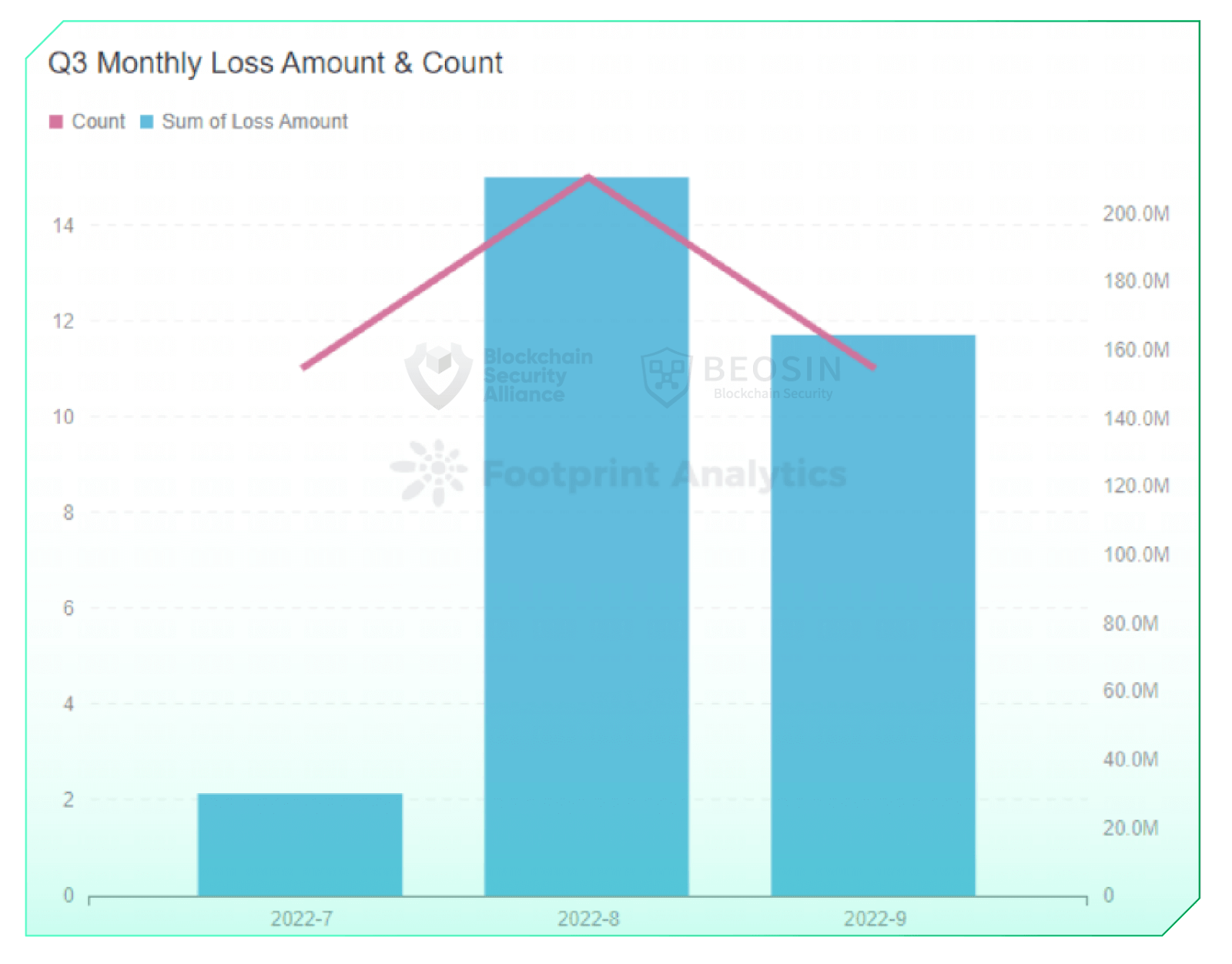
In Q3 2022, 37 major attacks were monitored in the Web3 space, with a total loss of approximately $405 million. There were two attacks with losses of $100 million or more, three attacks with losses of $10 million or more, and 14 attacks with losses of $1 million or more. The security incidents with over $100 million in losses were Nomad Bridge ($190 million) and Wintermute ($160 million).
August 2022 was the most active month for hackers in the quarter, with losses of around $210.62 million. Total losses from attacks in July were $30.05 million, making it the lowest amount of losses in a month since 2022.
3 Types of rekt projects
Cross-chain bridges and DeFi projects account for 92% of the loss amount

In the third quarter of 2022, three cross-chain bridge attacks resulted in a total loss of approximately $190.25 million; 22 attacks in the DeFi space resulted in a total loss of $186.79 million. Approximately 92% of the attack loss amount came from the cross-chain bridge and DeFi protocols.
As of September 2022, there were 10 major cross-chain bridge security incidents in 2022, with over $1.4 billion in losses. Cross-chain bridges were the most affected area by attacks in 2022.
In addition to cross-chain bridges and DeFi protocols, other types of projects attacked this quarter included NFTs, exchanges, DAOs, wallets, and MEV bots, making their overall types more diverse than in the previous quarter.
"
4 Loss amount by chain
Losses on Ethereum amount to $374.3 million
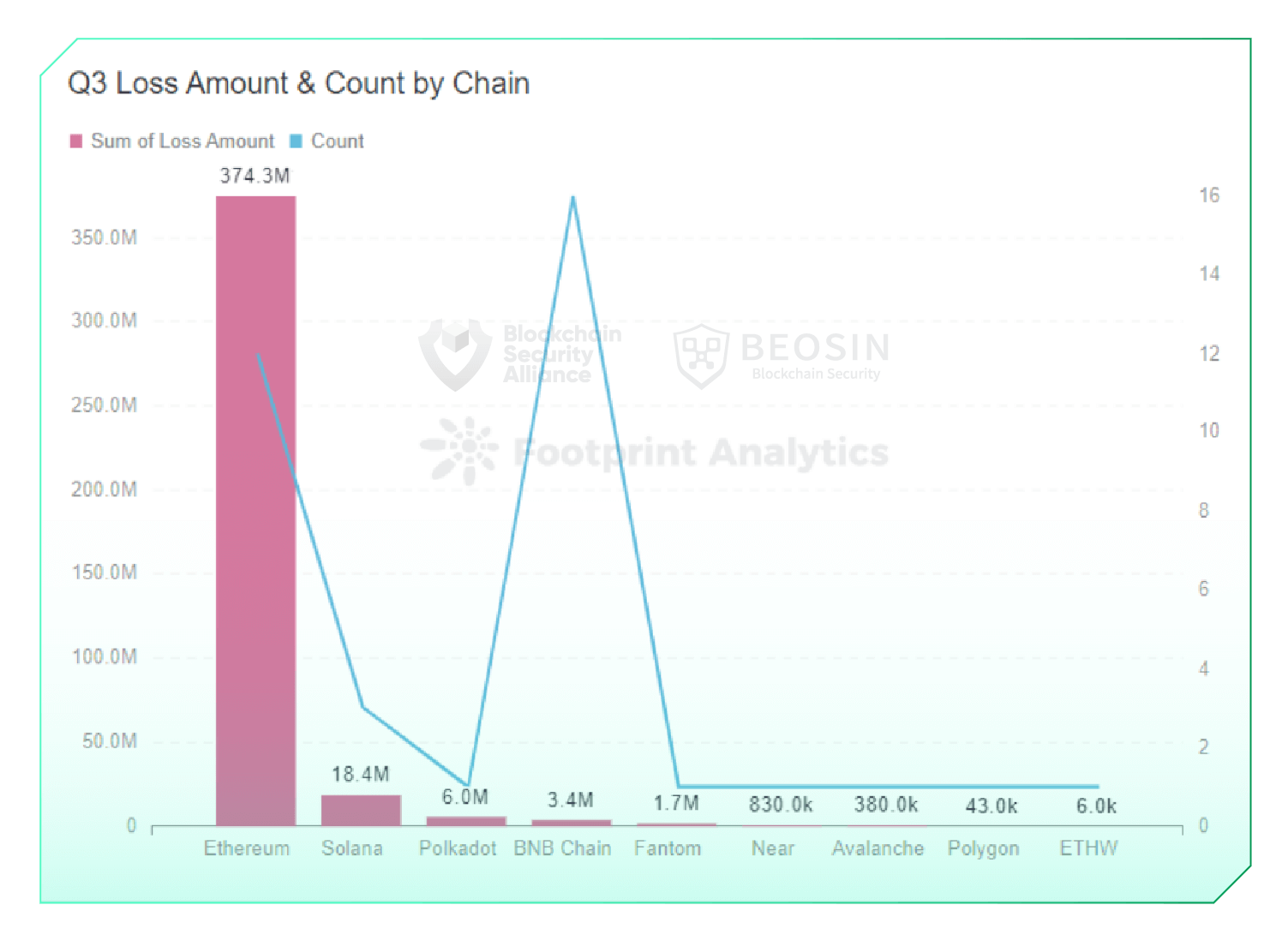
12 major attacks occurred on Ethereum this quarter, with a total loss of $374.28 million, ranking first among all chains. Solana lost $18.37 million from 3 exploits.
Chains with major attacks in two consecutive quarters include Ethereum, BNB Chain, Fantom, and Avalanche.
BNB Chain saw the most attacks, with 16 exploits, and their corresponding projects are all unaudited. The amount of money involved in these 16 exploits is relatively small, with 14 incidents involving a single loss of less than $500,000.
After experiencing a sharp drop in TVL from May to June, the trend of TVL across chains stabilized this quarter. TVL showed a slight upward trend in the period from late July to early August, which was also the period with the most attacks and loss amount this quarter. The crypto market generally moved slightly downward in September. After the Ethereum merge on September 15, the Ethereum TVL saw a continuous slight decline.
5 Analysis of Attack Types
92% of the lost amount was caused by contract vulnerability exploits and private key compromise
In the third quarter, contract exploits continued to be the most common attack type. About 15 attacks are contract vulnerability exploits, accounting for 40.5 percent of the total number. Total losses from contract vulnerabilities amounted to $201.6 million, or 50.9 percent of total losses.
The four private key compromises this quarter resulted in approximately $167.24 million in losses, the second largest amount of losses after contract vulnerability exploits.
Compared with the previous quarter, the types of attacks in this quarter were more diverse. New attack types that emerged this quarter include BGP hijacking, misconfiguration, and supply chain attacks.
By contract vulnerabilities, the main vulnerabilities exploited this quarter include: validation issues, reentrancy, permission issues, improperly designed business logic or functions, and overflow vulnerabilities. These vulnerabilities are all discoverable and fixable during the audit phase.
6 Typical Security Incident Recap
6.1 Nomad Bridge $190 Million Incident
On August 2, Nomad Bridge, a cross-chain platform that supports asset transfers across Ethereum, Moonbeam, Avalanche, Evmos and Milkomeda, suffered a massive hack that cost the project $190 million.
6.2 Slope Wallet Incident on Solana
On August 3, a large-scale Slope wallet theft incident occurred on Solana, with losses estimated at around $6 million.
6.3 Wintermute Private Key Compromise Incident
On September 20, crypto market maker Wintermute was attacked with a loss of $160 million due to a private key compromise.
7 Fund Flow Analysis
Approximately $204.2 million in stolen funds flowed into Tornado Cash
On August 8, the US Department of the Treasury’s Office of Foreign Assets Control (OFAC) sanctioned Tornado Cash, prohibiting U.S. individuals or organizations from interacting with it. In the third quarter of 2022, approximately $204.2 million in stolen funds still flowed into Tornado Cash, representing 50.4 percent of the funds stolen in that quarter, which is lower than in the second quarter.
Approximately $182.3 million of the stolen funds remained in the hacker’s address as the balance. Some stolen funds were bridged to addresses on other chains, and this portion is still counted as the hacker’s address balance.
About $16.6 million of assets were recovered through on-chain negotiations and unsolicited returns from white hat hackers. In the third quarter of 2022, only about 4% of the stolen funds were recovered, a much lower percentage than in the second quarter.
Around $1.92 million of stolen assets flowed into exchanges such as Binance and FixedFloat. Such incidents generally involved a small number of assets (usually around $10K to $100K), and the hackers transferred the stolen funds to the exchanges immediately after the attack, resulting in the projects failing to contact the exchanges in time to freeze the funds.
8 Project Audit Analysis
Only 40% of the projects were audited
In 2022, the percentage of rekt projects that were audited were: 70% in the first quarter, 52% in the second quarter, and 40% in the third quarter. The percentage of unaudited rekt projects shows an increasing trend quarter by quarter.
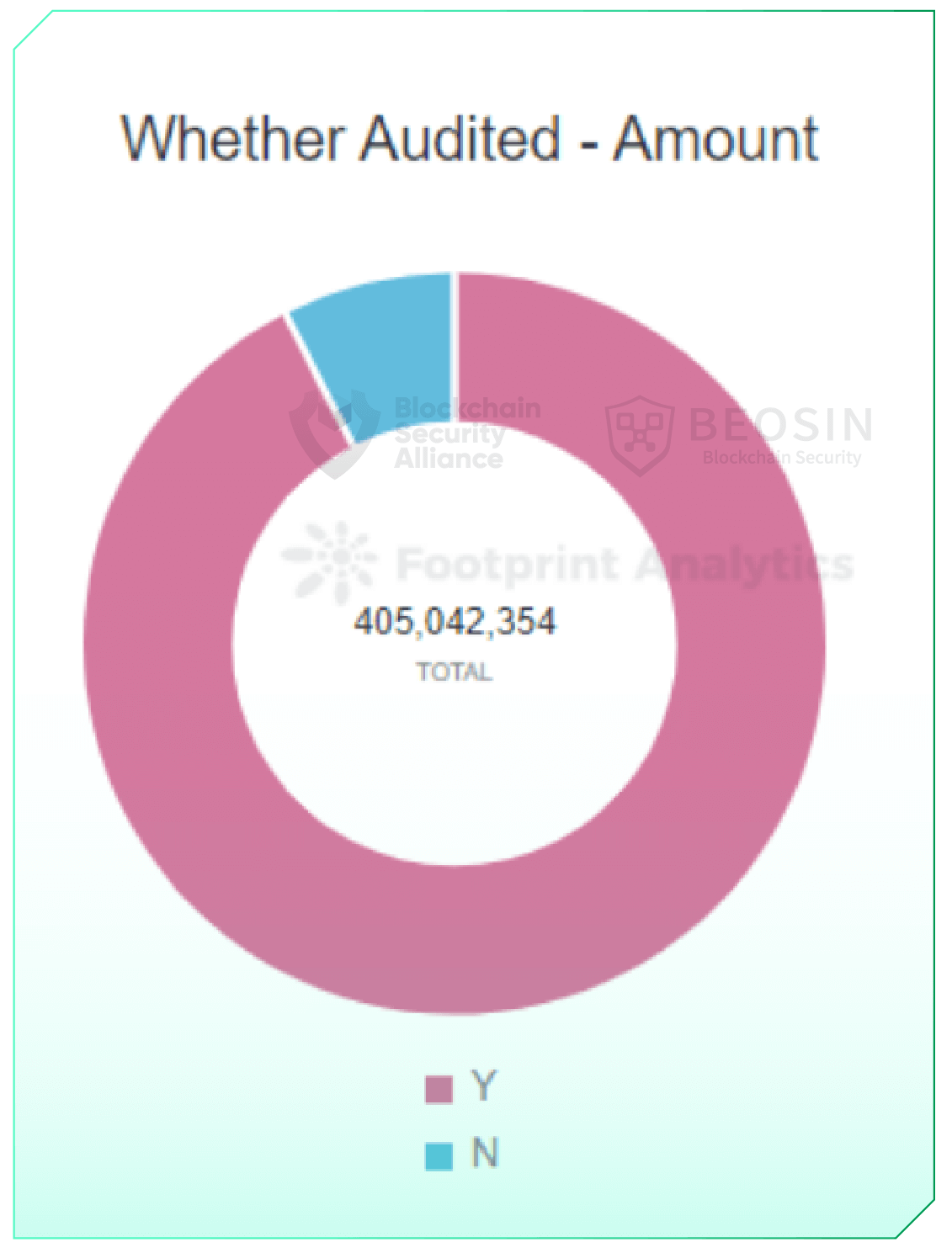
Of all the rekt projects, the audited projects lost a total of $ 375.48 million, and the unaudited projects lost about $ 29.56 million in attacks. At first glance, it might seem that audits did not serve to protect the safe operation of the projects. However, a deeper analysis shows that most of these audited projects were attacked by non-contractual level issues such as private key compromise, supply chain attacks, DNS attacks, BGP hijacking, and misconfiguration. Among the unaudited projects, 85% were caused by contract vulnerabilities or flashloan attacks.
It can be seen that professional audits are still effective in securing the project at the contract level to some extent. However, the safe operation of a protocol also requires a good job of offline risk control, safekeeping of the private key, being alert to traditional network security attacks, and using third-party components carefully. Of course, in this quarter, there are also some vulnerabilities that should have been discovered in the audit phase but were not presented in the audit report, so it is recommended that the project seek a professional security company to conduct the audit.
Data source
Download the full report:
About Blockchain Security Alliance
The Blockchain Security Alliance was launched by several units with diverse industry backgrounds, including university institutions, blockchain security companies, industry associations, fintech service providers, etc. The first batch of the alliance council includes Beosin, SUSS NiFT, NUS AIDF, BAS, FOMO Pay, Onchain Custodian, Semisand, Coinhako, ParityBit, and Huawei Cloud. The current members include: Huobi University, Moledao, Least Authority, PlanckX, Coding Girls, Coinlive, Footprint Analytics, Web3Drive, and Digital Treasures Center. The members of the Security Alliance will work and cooperate together to continuously secure the global blockchain ecosystem with their own technical strengths. The Alliance Council also welcomes more people in blockchain-related fields to join and jointly defend the security of the blockchain ecosystem.
 cryptoslate.com
cryptoslate.com