Camera and lens maker Canon has had its internal network and company services crippled via a ransomware attack-leading to 10 terabytes of data being stolen from the company's internal servers.
According to BleepingComputer, which reported the story first, ransomware group Maze has taken credit for the attack. A spokesperson for the group told the site it had stole "10 terabytes of data, private databases etc" from Canon, but declined to name specifics. BleepingComputer was able to correlate details of the attack with a source inside the company, who shared an IT notification stating that Canon is experiencing “wide spread system issues affecting multiple applications, Teams, Email, and other systems may not be available at this time.”
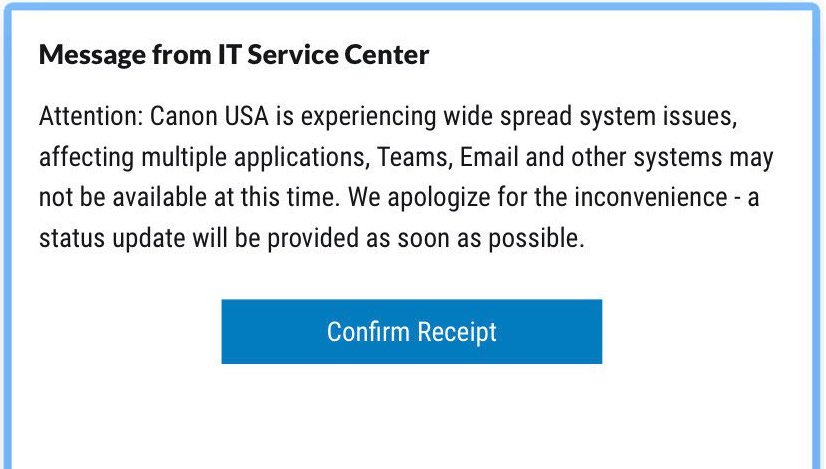
A notice from Canon's internal IT team about system outages (Source: Canon)
Who is Maze?
Maze is a ransomware group that has a sophisticated and resilient strain of Windows ransomware. The group is notorious for its threats to “dox” companies if they don’t pay up, publishing reams of data which often includes sensitive internal emails and personnel records.
The Maze ransomware gang recently published nearly 50 gigabytes of data it had stolen from LG and Xerox after the two companies declined to pay the requested ransom. Maze has threatened to publish the companies’ data to a “leak website” allowing the public to have access, but it’s not clear if Maze has gone ahead with the threat.
This is a significant change in operation from how most Malware operates; usually, it's the threat of having the files permanently locked away to incentivize firms to cooperate. Travel firm CWT, for instance recently paid out $4.5 million in Bitcoin to unlock 2TB of files, including financial reports, security documents and employees’ personal data such as email addresses and salary information, according to Reuters. Initially, the hackers demanded $10 million, but citing Covid-19’s impact on the travel industry the firm could only afford to pay up $4.5 million.
Ransomware attacks and payments increase in 2020
Despite an economy ravaged by Covid-19, the ransomware industry is seeing record profits thanks to both the success of high-profile attacks, such as the $10 million heist of Garmin’s servers, and the frequency of attacks on small to medium-sized enterprises.
According to security research firm Coveware, the average ransomware payment during the second quarter of the year was $178,254, a 60% leap from the $111,605 average in Q1.
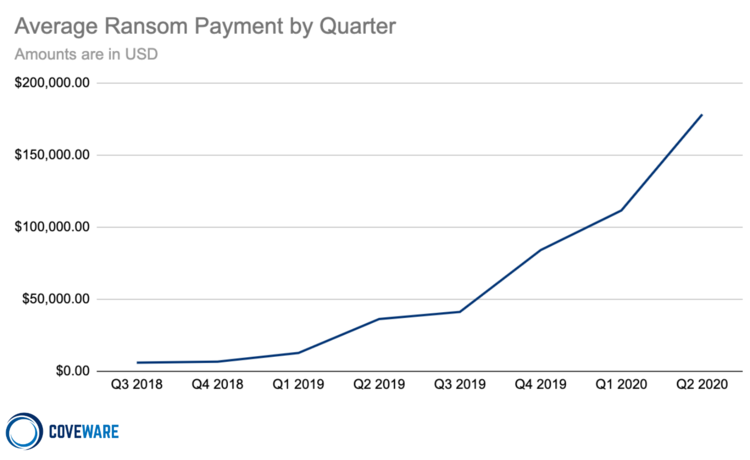
Coveware cites the rise of what it calls “big game hunting”, as in going after large enterprises, instead of “opportunistic spray-and-pray threat actors” that might target individuals or the smallest of firms. Its research shows that 55% of total enterprise attacks took place on companies with less than 100 employees.
Coveware says that Bitcoin — not privacy coins like Monero or Zcash — remains the most common method of paying ransom with 96% of transactions occurring in that currency.
 decrypt.co
decrypt.co