On March 13, Nopara73, an employee at Wasabi Wallet and a Bitcoin developer, announced on Twitter that users of Wasabi were under a dust attack. He also added that the attack was successful and that the dust would be hidden in the next release.
He stated,
“Wasabi users are under dust attack and it seems to be somewhat successful. About half of them don’t mind joining together some of their dusts, exposing the links between their mixed outputs (not the mixes though.) I’ll hide the dust in the next release.”
According to a Medium article by Matt B, dust is the “creation of minuscule transactions,” used to spam Bitcoin network or to “pepper” addresses with “tiny UTXOs.” Alpha Zeta, a Twitter user, explained that a dust attack was similar to a scenario where a third-party is placing a tracking device on a user’s UTXOs.
Here, a small amount of Bitcoin is sent to the user’s wallet, which can be used to track payments made by the address with those small amounts. She further added that it was an attempt at deanonymizing users. However, Nopara73 stated that this attack was different from before,
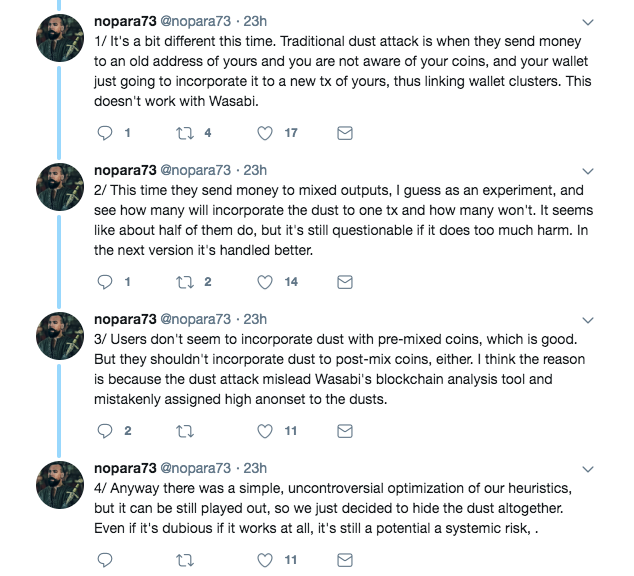
Source: Twitter
drbruyne, the moderator of r/Monero said,
“Even though dust attacks are technically still feasible in Monero, they are significantly more difficult to execute because, in Monero, public addresses do not appear on the Blockchain. By contrast, in Bitcoin, due to public addresses being visible on the blockchain, this attack is easily performed and can basically affect every address.”
SamsungGalaxyPlayer, an XMR contributor, stated on Reddit that a similar attack was possible on Monero. However, such an attack would be “far less significant,” the contributor said. The Redditor stated that since the addresses are not visible when it comes to Monero, dust attack can’t be used to target a random user.
“2. Monero’s ring signatures provide some built-in protection. It’s as if every dust output is mixed. The closest thing we have to worry about is the “poisoned output” (EAE) attack […]”
 ambcrypto.com
ambcrypto.com